Researchers Observed Visual Studio Code Extensions Stealing Users’ Sensitive Data
ReversingLabs has uncovered a series of Visual Studio Code (VS Code) extensions designed to transfer sensitive information from unsuspecting users.
This discovery highlights the growing trend of supply chain attacks increasingly targeting open-source repositories and platforms.
The threat landscape has seen a dramatic 1300% increase in supply chain attacks, with malicious actors exploiting public repositories to introduce compromised packages into the development cycle.
ReversingLabs has been at the forefront of monitoring these repositories, such as npm and PyPI, and has recently expanded its vigilance to include the VS Code Marketplace.
Malicious Extensions on VS Code Marketplace
The VS Code Marketplace, a hub for developers to share and install extensions, has historically been less affected by malicious activities.
Run Free ThreatScan on Your Mailbox
AI-Powered Protection for Business Email Security
Trustifi’s Advanced threat protection prevents the widest spectrum of sophisticated attacks before they reach a user’s mailbox. Try Trustifi Free Threat Scan with Sophisticated AI-Powered Email Protection .
However, ReversingLabs’ recent investigation has revealed multiple extensions linked to a single author, VSAnalysistest, that were engineered to steal data.
These extensions, including clipboard-helper-vscode, code-ai-assistant; codegpt-helper, and mycodegpt-assistant, were promptly removed from the marketplace following their detection.
 Malicious Extension Code Snippet
Malicious Extension Code Snippet
Disguised Threats and Data Exfiltration
The extensions were deceptively simple, with some masquerading as tools to enhance clipboard functionality or improve coding efficiency.
However, they harbored malicious intent, such as exfiltrating clipboard data or phishing for GitHub credentials via Discord webhooks.
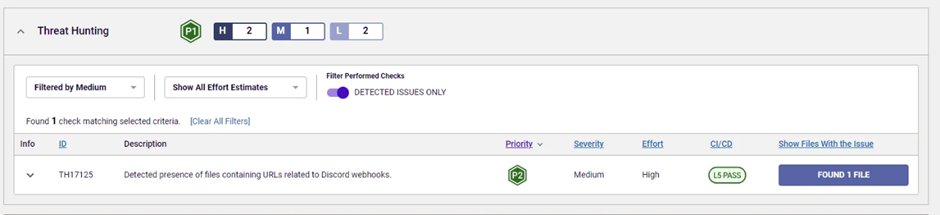 Threat hunting policy
Threat hunting policy
Limited Impact but a Warning Sign
Although the impact of these extensions was limited due to their short lifespan and low download numbers, their presence serves as a cautionary tale for developers and security professionals.
It underscores the need for vigilance against software supply chain attacks, even on less popular platforms like the VS Code Marketplace.
Developers are encouraged to conduct thorough security assessments of public libraries and extensions before incorporating them into their projects.
Tools like ReversingLabs Spectra Assure are available to assist developers in ensuring their code remains secure and free from malicious content.
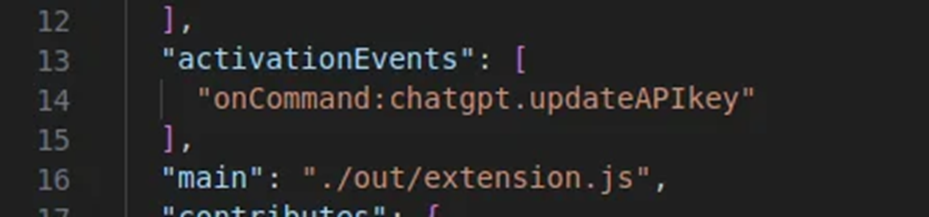 Activation Events in Malicious Extension
Activation Events in Malicious Extension
The discovery of these malicious VS Code extensions is a stark reminder that the threat of supply chain attacks is ever-present.
As attackers devise new methods to infiltrate software ecosystems, the community must remain proactive in safeguarding against these insidious threats.
IOCs
unique_identifier
version
VSAnalysistest.clipboard-helper-vs code
VSAnalysistest.clipboard-helper-vscode
0.0.1
edf04024c6e0a8927f04a26edcde4374b365e16d
VSAnalysistest.code-ai-assistant
0.0.2
14f4a6f3e872c3367e6ddec16a2b183176a091c8
VSAnalysistest.code-ai-assistant
0.0.1
c26fd1f6c993c6340712de86ec2b11f2f5e0535a
VSAnalysistest.codegpt-helper
0.0.1
3aac5b632e1ab6802f58237aeaaf5d0a6d491a44
VSAnalysistest.codegpt-helper
0.0.2
c02663d6c042f191c4d60789b068916469afbf3c
VSAnalysistest.mycodegpt-assistant
0.0.1
c8e2bbd712de025620720d0febab02cfbb97f4bf
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.
The post Researchers Observed Visual Studio Code Extensions Stealing Users’ Sensitive Data appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
posted by pod_feeder
%20(1).webp)
There are no comments yet.