“The biggest network security threat today is a remote code execution exploit for Intel’s Management Engine.”
“Every computer with an Intel chipset produced in the last decade would be vulnerable to this exploit, and RCE would give an attacker full control over every aspect of a system.
If you want a metaphor, we are dinosaurs and an Intel ME exploit is an asteroid hurtling towards the Yucatán peninsula.” (https://hackaday.com/tag/intel-me/)
Intel might have installed – over the course of at least a decade (to this day?) a closed source backdoor in your computer’s firmware, that might never receive updates and is hard to remove.
Once this backdoor is fully cracked, everyone (Russia, China and North Korea) can use it.
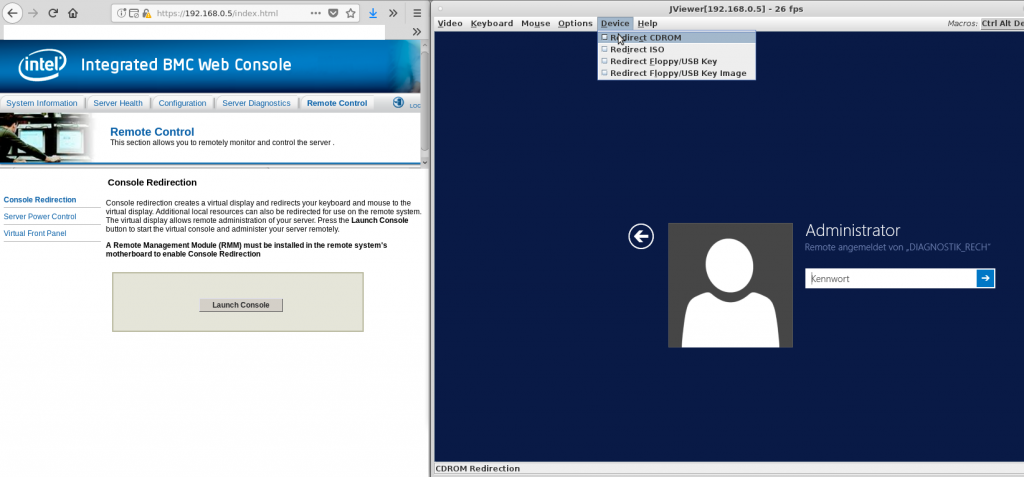
Having remote control over a server down to the BIOS is a neat feature.
Hackers think so too.
Because a firmware is sometimes hard to update.
BIOS-UEFI updates need to be as easy to install than OS updates.
There are even parts of Intel ME that can not be updated at all (yet) because they are encrypted & signed and the system won’t start if they are missing (security by obscurity).
another dramatic way to put it:
“The biggest network security threat today is a remote code execution exploit for Intel’s Management Engine.”
“Every computer with an Intel chipset produced in the last decade would be vulnerable to this exploit, and RCE would give an attacker full control over every aspect of a system.
If you want a metaphor, we are dinosaurs and an Intel ME exploit is an asteroid hurtling towards the Yucatán peninsula.” (https://hackaday.com/tag/intel-me/)
Currently the OS must be hacked or USB access (“physical access equals root access”) before it is possible to malware very deeply in the system = having this guy say: “only solution” “shredder mainboard”
But it might be just a matter of time, until new attack vectors are found, that allow exploit over network, maybe even in the security-nightmare language that every browser runs: JavaScript? X-D (just turn it off globally thanks!)
https://www.golem.de/news/conti-ransomware-gruppe-arbeitet-an-exploit-fuer-intel-me-2206-165848.html
(Conti is a hacker group associated with Russia)
https://www.golem.de/news/security-das-intel-me-chaos-kommt-2003-147099.html
https://www.golem.de/news/security-hackern-gelingt-vollzugriff-auf-intel-me-per-usb-1711-131065.html
Intel ME: Will Intel deliver updates? I hope so. Otherwise: Seriously sue intel to put your IT hardware at danger of being destroyed PERMANENTLY.
As it has happened with those KA-SAT satellite modems.
solutions anyone?
Yes multiple hard one’s.
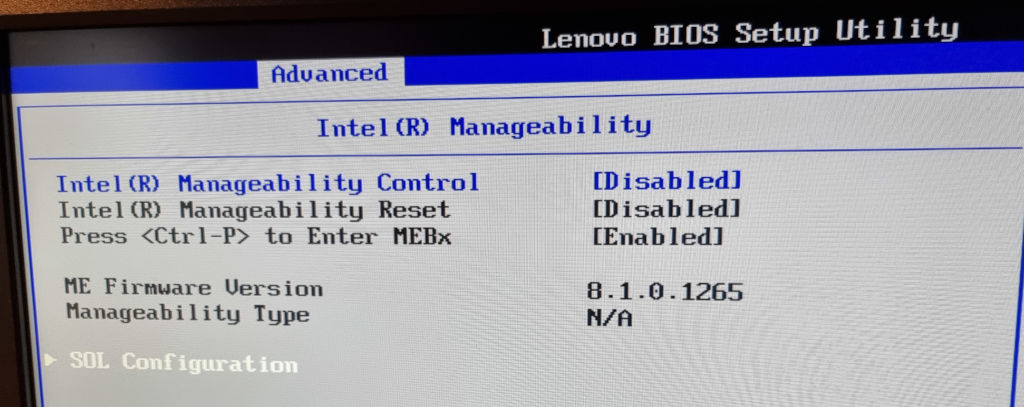
- try turning AMT BMC Intel ME off in the bios
- on some systems BMC can be disabled with a jumper on the motherboard
- Flash GNU Linux to the BIOS! (CoreBoot, LibreBoot with the Lenovo x60s no problem, with newer notebooks / PCs probably more effort)
- “Just use AMD”, yes better but according to this video only a partial solution?
intel needs to work with it’s damaged customers to fix this mess
Or be sued for every hack and every ransomware attack and every downtime and every destroyed motherboard.
seriously.
open source backdoors instead of closed source backdoors!
ok ideally no backdoors at all?
“Intel had already found the vulnerability (CVE-2019-0090) itself last year, described only as a privilege escalation and tried to fix a possible attack vector.
According to PT, however, there are probably other attack vectors and the real problem in ROM still remains, as this part cannot be updated.
This is the preliminary culmination of an embarrassment on the part of Intel, which the manufacturer is trying to sell as security.
By now at the latest, Intel should mothball the concept of a proprietary ME and work on the open hardware security chip that Google“
“Customers, users and Intel would be the winners.”
translated from: https://www.golem.de/news/security-das-intel-me-chaos-kommt-2003-147099.html
“Together with partners, Google has announced the Open Titan project.
The goal is a completely openly designed chip based on RISC-V, which is to be used as root-of-trust in many different devices.”
links:
https://www.rapid7.com/blog/post/2013/07/02/a-penetration-testers-guide-to-ipmi/
#linux #gnu #gnulinux #opensource #administration #sysops #cybersec #itsec #cyber #intel #intel-me #intelme
Originally posted at: https://dwaves.de/2022/06/10/russias-conti-working-on-exploits-for-intel-me-bmc-amt-ipmi-intel-me-the-biggest-security-fuck-up-in-computing-history-sue-intel/
There are no comments yet.