DarkGate Malware Abusing Cloud Storage & SEO Following Delivery Over Teams
DarkGate loader delivery surged after the Qakbot takedown, with financially motivated actors like TA577 and ransomware groups (BianLian, Black Basta) using it to target financial institutions (US, Europe) for double extortion.
It establishes an initial foothold and deploys info-stealers, ransomware, and remote access tools to maximize data exfiltration and extortion gains by utilizing legitimate channels (DoubleClick ads, cloud storage) and phishing emails for distribution.
Overview of DarkGate version 5 activity
Similarities with IcedID delivery methods suggest that threat actors may be cooperating or sharing their tradecraft.
@import url(‘https://fonts.googleapis.com/css2?family=Poppins&display=swap’); @import url(‘https://fonts.googleapis.com/css2?family=Poppins&family=Roboto&display=swap’); { margin: 0; padding: 0; text-decoration: none; } .container{ font-family: roboto, sans-serif; width: 90%; border: 1px solid lightgrey; padding: 20px; background: linear-gradient(2deg,#E0EAF1 100%,#BBD2E0 100%); margin: 20px auto ; border-radius: 40px 10px; box-shadow: 5px 5px 5px #e2ebff; } .container:hover{ box-shadow: 10px 10px 5px #e2ebff; } .container .title{ color: #015689; font-size: 22px; font-weight: bolder; } .container .title{ text-shadow: 1px 1px 1px lightgrey; } .container .title:after { width: 50px; height: 2px; content: ‘ ‘; position: absolute; background-color: #015689; margin: 20px 0; } .container h2{ line-height: 40px; margin: 5px 3px; font-weight: bolder; } .container a{ color: #170d51; } .container p{ font-size: 18px; line-height: 30px; margin: 10px 0; } .container button{ padding: 15px; background-color: #4469f5; border-radius: 10px; border: none; background-color: #00456e ; font-size: 16px; font-weight: bold; margin-top: 5px; } .container button:hover{ box-shadow: 1px 1px 15px #015689; transition: all 0.2S linear; } .container button a{ color: white; } hr{ / display: none; / } .listWrapper { padding-left: 4rem; /*list-style-type: none;/ } .listWrapper li { /padding-left: 2rem; background-image: url(star.svg);/ background-position: 0 0; line-height: 2rem; background-size: 1.6rem 1.6rem; background-repeat: no-repeat; }
Download Free CISO’s Guide to Avoiding the Next Breach
Are you from The Team of SOC, Network Security, or Security Manager or CSO? Download Perimeter’s Guide to how cloud-based, converged network security improves security and reduces TCO.
Understand the importance of a zero trust strategy
Complete Network security Checklist
See why relying on a legacy VPN is no longer a viable security strategy
Get suggestions on how to present the move to a cloud-based network security solution
Explore the advantages of converged network security over legacy approaches
Discover the tools and technologies that maximize network security
Adapt to the changing threat landscape effortlessly with Perimeter 81’s cloud-based, unified network security platform.
Download Perimeter 81 Free PDF Guide </html
DarkGate is a malware-as-a-service advertised in June 2023 that offers remote access, data theft, and privilege escalation by using multiple techniques to evade, including a custom crypter, polymorphism, and anti-VM.
Persona RastaFarEye is advertising DarkGate on a cybercrime forum.
It also utilizes LOLBAS tools to download a malicious AutoIt script that decrypts the DarkGate payload, injects it into a process, and establishes persistence through registry keys and a rootkit module.
*DarkGate infection chain through PDF lure. *
Attackers primarily target financial institutions like BDK, a major German bank, using phishing emails with lures relevant to the target’s industry and delivering the DarkGate payload through embedded links in PDF attachments.
*The delivered malicious PDF attachment targeted the BDK. *
The links redirect victims to download pages hosted on compromised websites.
To evade detection, DarkGate operators have incorporated innovative techniques like abusing DNS TXT records to execute malicious Windows commands that download and install the malware.
* Malware delivery similarities between DarkGate and IcedID.*
EclecticIQ analysts compared DarkGate and IcedID malware, finding shared tactics like obfuscated strings, using PING.exe to check internet connectivity, CURL.exe for downloading payloads, and decoy PDF documents.
They differed in execution tools (DarkGate: Cscript.exe, IcedID: Rundll32.exe) and payload types (DarkGate: VBS script, IcedID: disguised DLL).
Showing the example of DoubleClick Ad service abuse.
For DarkGate delivery, attackers abused open redirects in Google’s DoubleClick ads with emails containing links disguised as invoices.
Since January 2024, DarkGate has shifted to CAB and MSI formats, likely to evade detection.
DarkGate version 6.1.6 employs DLL side-loading for evasion, where a malicious DLL is loaded into legitimate applications (e.g., VLC, iTunesHelper) through a compromised MSI installer.
Dropped DarkGate payloads
The payload then decrypts itself using a key within a fake sqlite3.dll and drops a script into C:\temp, while decrypting again using a separate key and launching the final DarkGate payload.
Decrypted configuration reveals the command-and-control server.
The version also features a new configuration decryption routine using XOR encryption to hide C2 server information and other operational parameters, making it more difficult for signature-based detection.
DarkGate is a Malware-as-a-Service (MaaS) that steals information like usernames, CPU information, and anti-virus information from the victim device after gaining an initial foothold.
Decrypted C2 activity showing the version of Darkgate.
It then uses Living Off the Land Binaries (LOLBAS) like wscript.exe and cscript.exe to execute a VBS script.
v
Network traffic analysis can be used to detect suspicious patterns like downloads from unusual domains or suspicious Curl.exe activity and YARA rules can also be used to detect the final payload on the infected device.
The IOCs include suspicious user agent strings, command and control (C2) server domains, payload downloader URLs with malicious zip files, and multiple file hashes, which can be used to identify infected systems, block malicious traffic, and improve threat detection.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.
The post DarkGate Malware Abusing Cloud Storage & SEO Following Delivery Over Teams appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
posted by pod_feeder
%20(1).webp)
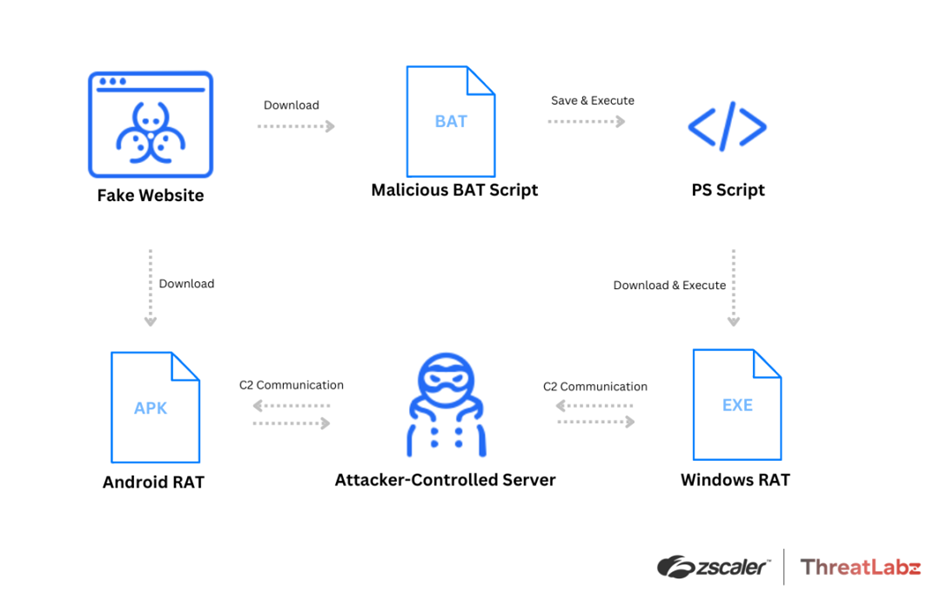
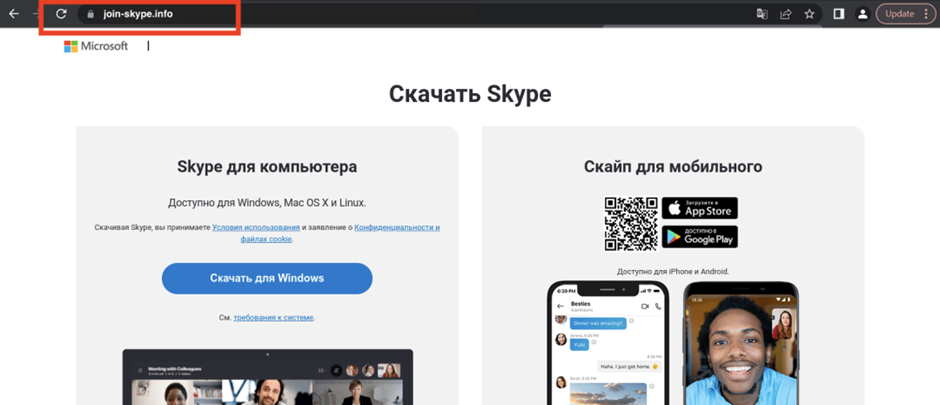 The fraudulent Skype website, with a fake domain meant to resemble the legitimate Skype domain. (Source urlscan.io.)
The fraudulent Skype website, with a fake domain meant to resemble the legitimate Skype domain. (Source urlscan.io.)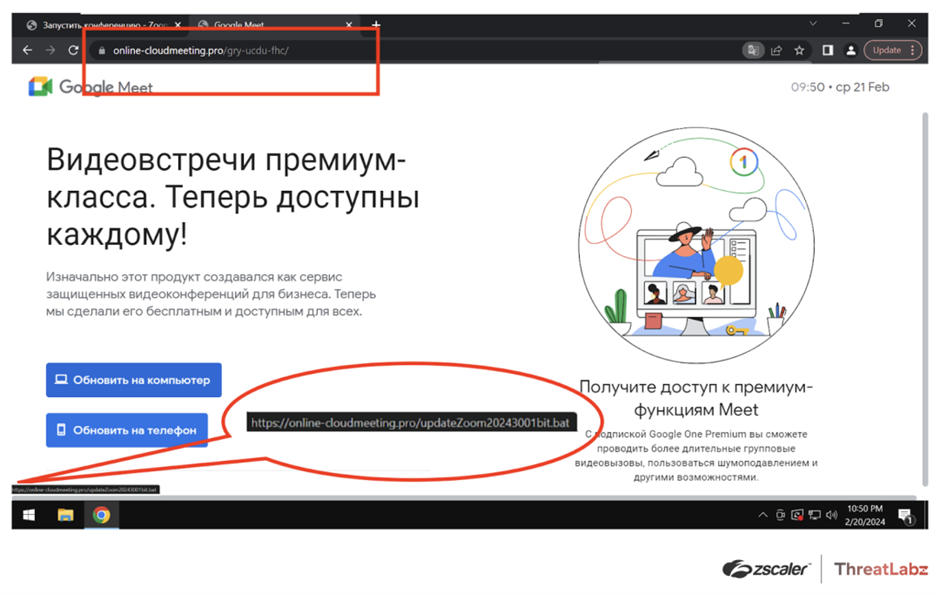 The fake Google Meet page, showing the fraudulent domain in the address bar for a fake Google Meet Windows application links to a malicious BAT file that downloads and executes malware. (Source: Zscaler)
The fake Google Meet page, showing the fraudulent domain in the address bar for a fake Google Meet Windows application links to a malicious BAT file that downloads and executes malware. (Source: Zscaler)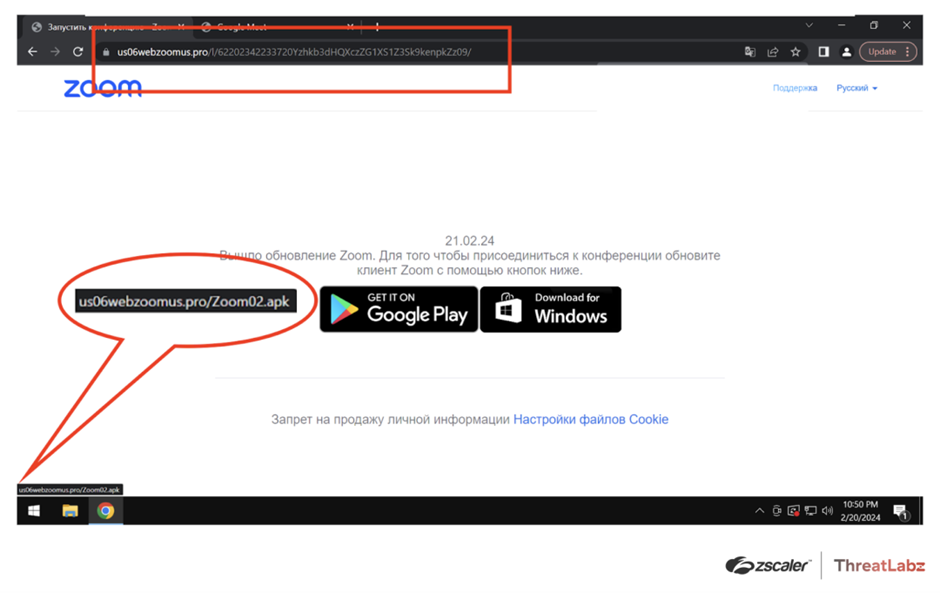 The fake Zoom page shows a domain similar to the real Zoom domain in the address bar and a link to the malicious APK file that contains SpyNote RAT when the Google Play button is clicked. (Source:
The fake Zoom page shows a domain similar to the real Zoom domain in the address bar and a link to the malicious APK file that contains SpyNote RAT when the Google Play button is clicked. (Source:  Example of additional malicious files hosted on the websites hosting fake online meeting applications. (Source: Zscaler)
Example of additional malicious files hosted on the websites hosting fake online meeting applications. (Source: Zscaler).webp)