The origins of Bitwarden and how it is fending off the tech giants
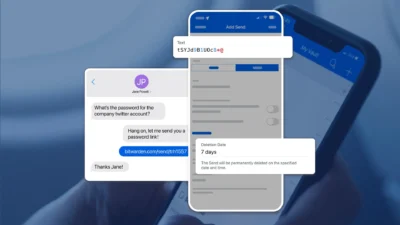
Kyle Spearrin had never developed a mobile app or browser extension when he started building Bitwarden as a fun side project in 2015.
Nearly nine years later, Spearrin’s humble attempt at a free, open-source password manager has become one of the most popular ways to keep online accounts secure. Wirecutter, PCWorld, PCMag, and others say it’s the best free password manager, and CNet even calls it the best password manager overall. Bitwarden says it now has 8.5 million users, and it uses that audience to grow its enterprise subscription business. Bitwarden’s business side has tens of thousands of customers and helped fuel nearly 100% revenue growth last year, and the company now has roughly 200 employees.
“We really value that everyone should have access to a full-featured password management tool,” Spearrin says.
Very humble beginnings, and of course we’ve seen why tech giants like Apple, Google, etc embraced passkeys with such enthusiasm, as this would lock users into their ecosystem. Try using your Apple passkeys when migrating to say Android, or vice versa.
“If you are locked in with one vendor, you have a risk of being locked out of your account,” Magdanurov says. “Something can happen. Somebody can hack your account. Or their automated tools that block your account for violations can be triggered for some reason.”
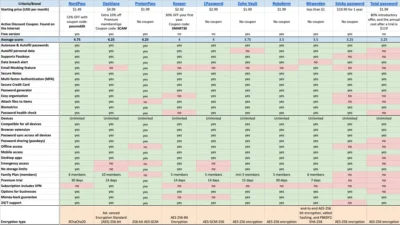
So, whilst it is true many tech giants have been improving their offerings around password management, Bitwarden is managing to stay a step or two ahead of them with newer innovative features (some I did not even know about). And of course, one can self-host Bitwarden too.
A lot can also be learnt from buy-outs like LastPass went through. The ownership does dictate the philosophy, or changes to it.
Although I’m eyeing out Proton Pass’ rapid developments (I’m a paying Proton user) I’m still a paid tier user of Bitwarden as right now they’re doing their things right, and what I really like is that their paid tier is not expensive at all. I just feel that I am supporting what they do.
See fastcompany.com/91117788/how-b…
#Blog, #bitwarden, #opensource, #passwords, #security, #technology