GNU Linux (Debian) 10 - how to access QNAP (TS-219P) NAS via NFSv4 - why QNAP has created a security mess - portmap query failed: RPC: Program/version mismatch / Protocol not supported

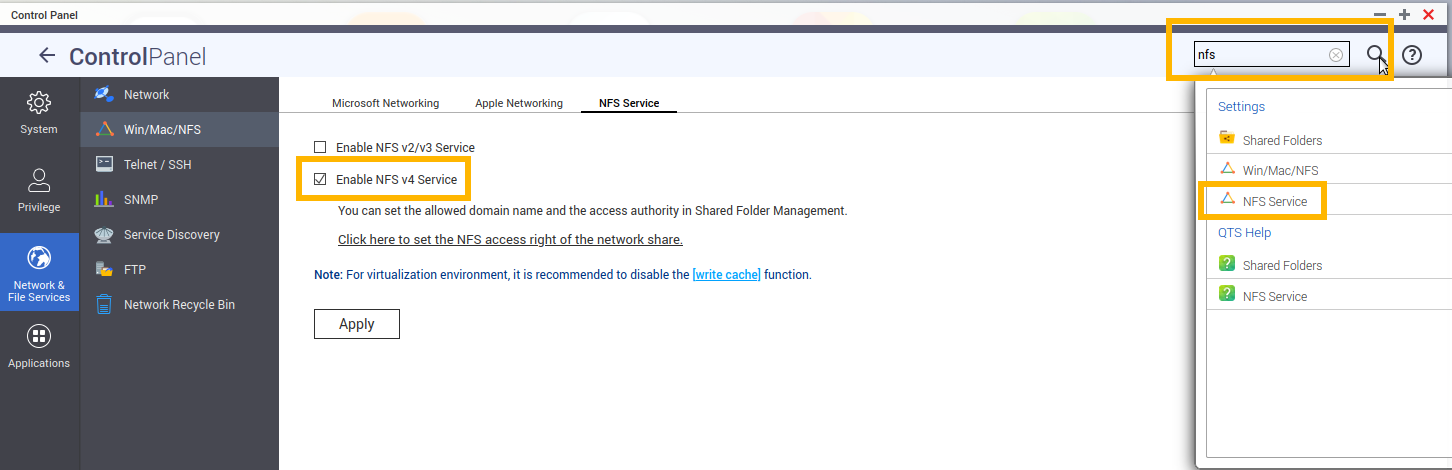
- create a new shared folder on the nas call it “data”
- enable NFSv4, disable NFSv3
- specify list of IPs that are allowed to access the NFSv4 share:
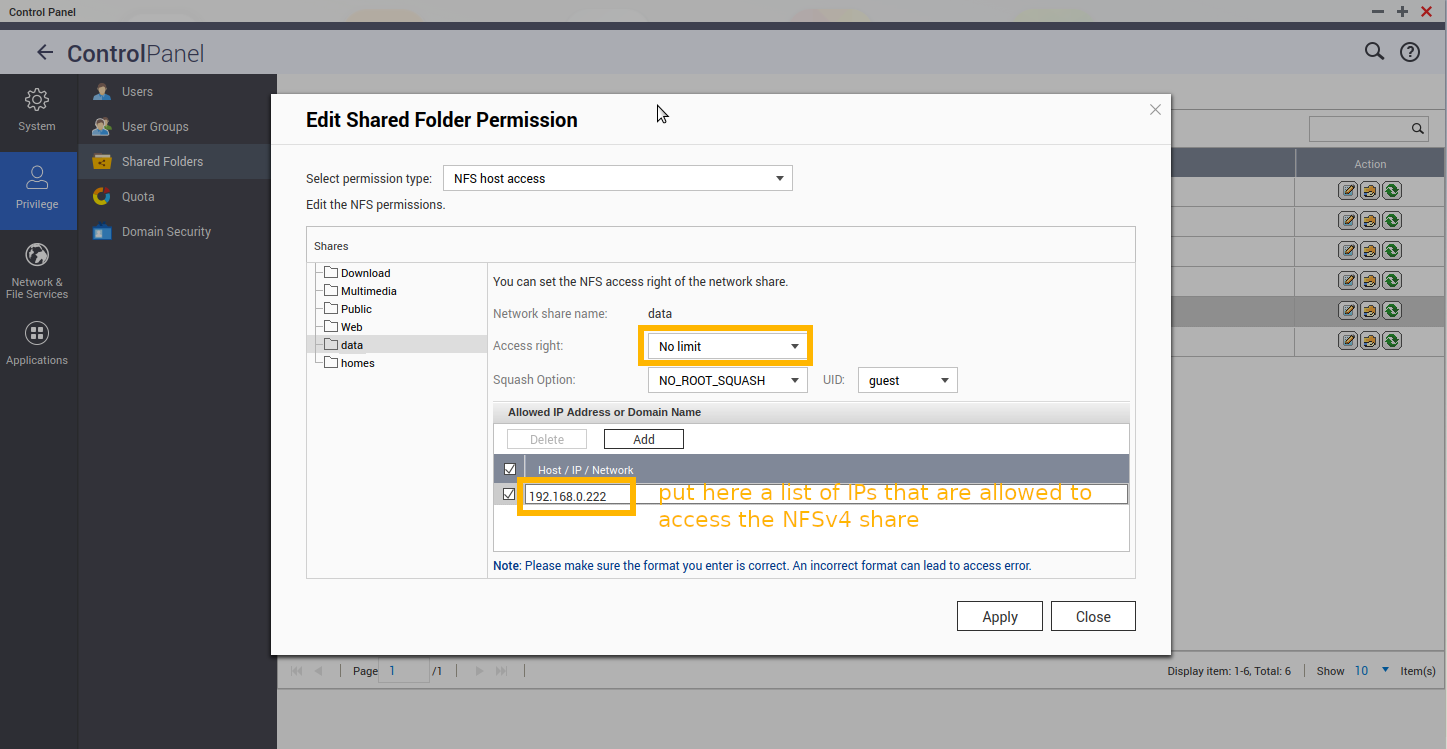 don’t forget to hit “Apply”
don’t forget to hit “Apply”- the idea is “anyway” to NAS<-directly-LAN-1000MBit->PC connect the NAS to the GNU Linux 10 based PC for maximum speed (PC will get fixed IP so no problem here)
<span style="color: #00ffff;">lsb_release -a</span>; # tested on
No LSB modules are available.
Distributor ID: Debian
Description: Debian GNU/Linux 10 (buster)
Release: 10
Codename: buster
su - root; # become root
# create mount point
<span style="color: #00ffff;">mkdir /media/user/nfs/</span>
# the actual mounting process
<span style="color: #00ffff;">mount -v -t nfs4 192.168.0.230:/data/ /media/user/nfs/
</span>
possible errors: portmap query failed: RPC: Program/version mismatch / Protocol not supported
in this case what fixed those errors, was to allow access from specific list of IPs:

mount.nfs4: timeout set for Mon Mar 14 16:32:09 2022
mount.nfs4: trying text-based options 'vers=4.2,addr=192.168.0.230,clientaddr=192.168.0.222'
mount.nfs4: mount(2): Protocol not supported
mount.nfs4: trying text-based options 'vers=4.1,addr=192.168.0.230,clientaddr=192.168.0.222'
mount.nfs4: mount(2): No such file or directory
mount.nfs4: trying text-based options 'addr=192.168.0.230'
mount.nfs4: prog 100003, trying vers=3, prot=6
mount.nfs4: trying 192.168.0.230 prog 100003 vers 3 prot TCP port 2049
mount.nfs4: portmap query retrying: RPC: Program/version mismatch
mount.nfs4: prog 100003, trying vers=3, prot=17
mount.nfs4: trying 192.168.0.230 prog 100003 vers 3 prot UDP port 2049
mount.nfs4: portmap query failed: RPC: Program/version mismatch
mount.nfs4: Protocol not supported
the QNAP itsec mess: NEVER ALLOW PUBLIC ACCESS TO USER’S QNAP NAS VIA INTERNET!
while QNAP THINKS it does goad by loading MASSIVE amounts of pre installed stuff on their devices and promising “your personal cloud” QNAP actually creates A GIANT SECURITY PROBLEM because users WRONGLY trusting that QNAP NAS DEVICES ARE SUPER SECURE GNU LINUX (BUSY)BOXES and then DIRECTLY make the NAS accessible via internet from outside via various (more or less secure protocols, SMB/FTP/NFS ALL NOT SECURE PROTOCOLS!)
QNAP NAS and NFS protocol are intended to be used behind a firewall within a company net to store only backups, not unique data that might get lost BECAUSE OF A FIRMWARE BUG. (it has happened before)
less is sometimes more:

some performance & security optimizations that should be done:
- go through ALL settings and disable ALL service that are not needed (Windows-Samba-Sharing, AFS Apple FileSharing, UPnP)
- furthermore: ssh into the nas and modify crontab to not start those services:
- ```
# every hour make sure mytranscode media bloatware is stopped!
0 * * * * /etc/init.d/QMediaService.sh stop
# every hour make sure cups service is stopped (not needed free ram for something else)
0 * * * * /etc/init.d/cupsd.sh stop
```
- run ps uax to checkout any unecessary service that might still be running & consuming resources
here is the output in this case:
<span style="color: #00ffff;">ps uax</span>
PID Uid VmSize Stat Command
1 admin 644 S init
2 admin SW [kthreadd]
3 admin SW [ksoftirqd/0]
6 admin SW< [khelper]
7 admin SW [kworker/u:1]
139 admin SW [sync_supers]
141 admin SW [bdi-default]
142 admin SW< [kblockd]
148 admin SW< [ata_sff]
158 admin SW [khubd]
160 admin SW [kethubd]
165 admin SW< [md]
258 admin SW [kswapd0]
259 admin SW [fsnotify_mark]
261 admin SW< [crypto]
358 admin SW [scsi_eh_0]
361 admin SW [scsi_eh_1]
365 admin SW [kworker/u:3]
374 admin SW [scsi_eh_2]
377 admin SW [scsi_eh_3]
388 admin SW< [orion_spi]
396 admin SW [mtdblock0]
400 admin SW [mtdblock1]
404 admin SW [mtdblock2]
408 admin SW [mtdblock3]
412 admin SW [mtdblock4]
416 admin SW [mtdblock5]
441 admin SW< [deferwq]
475 admin SW [flush-1:0]
578 admin 1276 S /bin/sh /sbin/hotplug usb
583 admin 1532 S /bin/sh /etc/hotplug/usb.agent
651 admin SW [md9_raid1]
688 admin SW [md13_raid1]
773 admin SW [kjournald]
1144 admin SW< [dm-block-clone]
1164 admin SW [mv_crypto]
1177 admin SW< [cryptodev_queue]
1209 admin SW< [rpciod]
1216 admin SW< [nfsiod]
1223 admin SW< [cifsiod]
1234 admin SW [fnotify]
1244 admin SW< [cfg80211]
1265 admin 472 S < qWatchdogd: keeping alive every 1 seconds...
1459 admin SW [flush-9:0]
1736 admin SW [kjournald]
1873 admin 980 S /sbin/modagent
1918 admin SW [md2_raid1]
2167 admin 1304 S /bin/sh /etc/init.d/mtp_run.sh
2310 admin 632 S /sbin/kerrd
2407 admin SW [md0_raid1]
2409 admin RWN [md0_resync]
2760 admin SW [jbd2/md0-8]
2761 admin SW< [ext4-dio-unwrit]
2821 admin 1688 S /sbin/hotswap
2826 admin 1428 S /sbin/qsmartd -d
3161 admin 5604 S < /usr/local/apache/bin/fcgi-pm -k start -f /etc/apache-sys-proxy.conf
3168 admin 6588 S < /usr/local/apache/bin/apache_proxy -k start -f /etc/apache-sys-proxy.conf
3169 admin 6588 S < /usr/local/apache/bin/apache_proxy -k start -f /etc/apache-sys-proxy.conf
3170 admin 6588 S < /usr/local/apache/bin/apache_proxy -k start -f /etc/apache-sys-proxy.conf
3171 admin 6588 S < /usr/local/apache/bin/apache_proxy -k start -f /etc/apache-sys-proxy.conf
3172 admin 6588 S < /usr/local/apache/bin/apache_proxy -k start -f /etc/apache-sys-proxy.conf
3188 admin 6512 S /usr/local/apache/bin/fcgi-pm -k start -f /etc/apache-sys-proxy-ssl.conf
3196 httpdusr 6904 S /usr/local/apache/bin/apache -k start -c PidFile /var/lock/apache.pid -f /etc/config/apache/apache.conf
3197 httpdusr 6904 S /usr/local/apache/bin/apache -k start -c PidFile /var/lock/apache.pid -f /etc/config/apache/apache.conf
3198 httpdusr 6928 S /usr/local/apache/bin/apache -k start -c PidFile /var/lock/apache.pid -f /etc/config/apache/apache.conf
3287 admin 3132 S sshd: admin@pts/1
3315 admin 1484 S -sh
3324 admin 1476 S bash
3358 admin 9544 S /usr/local/apache/bin/apache_proxys -k start -f /etc/apache-sys-proxy-ssl.conf
3398 admin 9472 S /usr/local/apache/bin/apache_proxys -k start -f /etc/apache-sys-proxy-ssl.conf
3404 admin 9424 S /usr/local/apache/bin/apache_proxys -k start -f /etc/apache-sys-proxy-ssl.conf
3420 admin 9140 S /usr/local/apache/bin/apache_proxys -k start -f /etc/apache-sys-proxy-ssl.conf
3421 admin 9164 S /usr/local/apache/bin/apache_proxys -k start -f /etc/apache-sys-proxy-ssl.conf
4017 admin 6588 S < /usr/local/apache/bin/apache_proxy -k start -f /etc/apache-sys-proxy.conf
# yes it runs a full blown mysql database server
<span style="color: #ff6600;"> 4244 admin 45236 S /usr/local/mariadb/bin/mysqld --defaults-file=/usr/local/mariadb/my-mariadb.cnf --basedir=/usr/local/mariadb --datadir=/share/MD0_DATA/.system/data --plugin-dir=/usr/local/mariadb/lib/</span>
4365 admin 2388 S /sbin/qpkgd -d0
4420 guest 1084 S /usr/sbin/dbus-daemon --system
5328 admin 2380 S /usr/local/sbin/_thttpd_ -p 58080 -nor -nos -u admin -d /home/httpd -c **.* -h 127.0.0.1 -i /var/lock/._thttpd_.pid
5609 admin 22128 S < /usr/local/apache/bin/apache_proxy -k start -f /etc/apache-sys-proxy.conf
5718 httpdusr 1148 S /sbin/lpb_scheduler -d
5760 admin 1560 S /sbin/genthd
5948 admin SW< [krfcommd]
5973 admin 1480 S /usr/sbin/bluetoothd
5982 admin 428 S /usr/sbin/agent --adapter hci0
6044 admin 1916 S /usr/local/sbin/remote_folder_daemon --reset
6202 admin 912 S /usr/sbin/ntpdated
6216 admin 1600 S /usr/sbin/upsutil
6478 admin 2756 S /usr/sbin/sshd -f /etc/config/ssh/sshd_config -p 1234
6744 admin 23660 S /usr/local/apache/bin/apache_proxys -k start -f /etc/apache-sys-proxy-ssl.conf
7211 admin 1348 S /usr/bin/lunportman
7264 admin 2080 S /sbin/bcclient
7347 admin 1944 S /sbin/picd
7350 admin 1724 S /sbin/gpiod
7355 admin 1868 S /sbin/hwmond
7432 admin 816 S N /usr/bin/rsyncd --daemon --sever-mode=1 --qnap-bwlimit
7728 admin 1880 S /sbin/hd_util
7730 admin 552 S /sbin/gen_bandwidth -r -i 5
7863 admin 1128 S /bin/sh /etc/init.d/klogd.sh start
7872 admin 1748 S qNoticeEngined: Write notice is enabled...
7885 admin 1304 S /sbin/qsyslogd
7893 admin 1392 S /sbin/qShield
7907 admin 1956 S qLogEngined: Write log is disabled...
7964 admin 460 S /bin/dd if=/proc/kmsg of=/mnt/HDA_ROOT/.logs/kmsg bs=1 count=1024000
8131 admin SW< [iscsi_eh]
8179 admin SW [qnap_et]
8250 admin 448 S /sbin/iscsid --config=/etc/config/iscsi/sbin/iscsid.conf --initiatorname=/etc/iscsi/initiatorname.iscsi
8251 admin 2248 S < /sbin/iscsid --config=/etc/config/iscsi/sbin/iscsid.conf --initiatorname=/etc/iscsi/initiatorname.iscsi
8296 admin 1512 S /sbin/vdd_control -d
8943 admin 820 S /usr/bin/portmap
9189 admin 232 S /usr/sbin/rpc.rquotad -p 30002
9465 admin 2476 S /usr/sbin/rpc.mountd -p 30000 -F
9628 admin SW [lockd]
9629 admin SW< [nfsd4]
9631 admin SW< [nfsd4_callbacks]
9633 admin SW [nfsd]
9634 admin SW [nfsd]
9635 admin SW [nfsd]
9636 admin SW [nfsd]
9637 admin SW [nfsd]
9638 admin SW [nfsd]
9639 admin SW [nfsd]
9640 admin SW [nfsd]
9775 admin 1440 S /usr/sbin/rpc.idmapd
9784 admin 1940 S /usr/sbin/rpc.statd -p 30001
9826 admin 1280 S /sbin/daemon_mgr
9886 admin 2012 S /usr/local/bin/qb_daemon -d 7
9906 admin 2048 S /usr/bin/qsyncman
10321 admin 2032 S /sbin/upnpcd -i 300
11289 admin 3860 S /usr/local/apache/bin/apache-dav -k start -f /etc/apache-dav-sys.conf
11296 admin 2024 S /usr/local/apache/bin/apache-dav -k start -f /etc/apache-dav-sys.conf
11516 admin 592 S /sbin/getty 115200 ttyS0
11731 admin 23484 S /usr/local/apache/bin/apache -k start -c PidFile /var/lock/apache.pid -f /etc/config/apache/apache.conf
12927 admin SW [kworker/0:1]
14999 admin 3136 S sshd: admin@pts/2
15024 admin 1488 S -sh
15291 admin 1568 S bash
15461 admin 8360 S /usr/local/apache/bin/apache_proxys -k start -f /etc/apache-sys-proxy-ssl.conf
16254 admin SW [kworker/0:2]
16963 admin SW [flush-9:9]
18716 admin 748 S /usr/sbin/crond -l 9 -c /tmp/cron/crontabs
18893 admin 8932 S /usr/local/apache/bin/apache_proxys -k start -f /etc/apache-sys-proxy-ssl.conf
19588 admin SW [kworker/0:0]
20944 admin 6764 S /usr/local/apache/bin/apache_proxys -k start -f /etc/apache-sys-proxy-ssl.conf
23461 admin SW [kworker/0:3]
23685 admin 400 S /bin/sleep 1
23686 admin 784 R ps uax
23687 admin 1848 R chartReq.cgi
23688 admin 1076 S /usr/local/sbin/_thttpd_ -p 58080 -nor -nos -u admin -d /home/httpd -c **.* -h 127.0.0.1 -i /var/lock/._thttpd_.pid
30445 admin SW [flush-9:13]
related articles:
https://dwaves.de/2021/10/11/gnu-linux-debian-how-to-setup-nfs-server-and-mount-nfs-share/
manpages:
mount.nfs4.man.txt
#linux #gnu #gnulinux #opensource #administration #sysops #qnap #nas #nfs #storage
Originally posted at: https://dwaves.de/2022/03/14/gnu-linux-debian-10-how-to-access-qnap-ts-219p-nas-via-nfsv4-why-qnap-has-created-a-security-mess-portmap-query-failed-rpc-program-version-mismatch-protocol-not-supported/