Hackers Claiming Breach of Five Eyes Intelligence Group (FVEY) Documents
A group of hackers has announced the release of sensitive documents purportedly belonging to the Five Eyes Intelligence Group (FVEY), a prominent intelligence alliance comprising Australia, Canada, New Zealand, the United Kingdom, and the United States.
The United States Department of State has launched an investigation into a possible cyber attack after confidential documents, which were reportedly obtained by a malicious actor, were leaked from a government contractor.
Breach Announcement on BreachForums
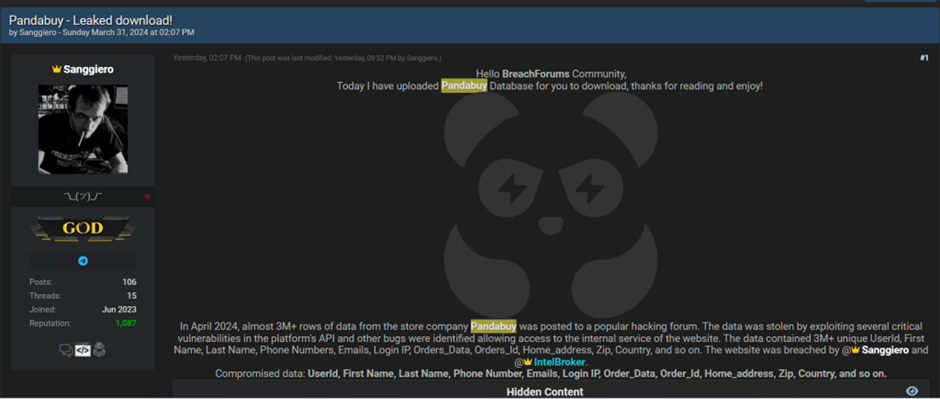
The announcement was made on a forum known as BreachForums, where a user with the handle “IntelBroker” posted a message to the community.
Run Free ThreatScan on Your Mailbox
AI-Powered Protection for Business Email Security
Trustifi’s Advanced threat protection prevents the widest spectrum of sophisticated attacks before they reach a user’s mailbox. Try Trustifi Free Threat Scan with Sophisticated AI-Powered Email Protection .
The post, dated April 2, 2024, claims that the data was obtained by infiltrating Acuity Inc, a company alleged to work closely with the US government and its allies.
According to a recent tweet by HackManac, the alleged security breach at Acuity Inc has resulted in the exposure of highly sensitive intelligence documents belonging to the Five Eyes Intelligence Group (FVEY).
[
](https://twitter.com/hashtag/DataBreach?src=hash&ref_src=twsrc%5Etfw)
Alert ⚠️
🇺🇸
[
](https://twitter.com/hashtag/USA?src=hash&ref_src=twsrc%5Etfw)
: Alleged Acuity Inc breach leads to leak of sensitive Five Eyes Intelligence Group (FVEY) documents.
The threat actor group consisting of IntelBroker, Sanggiero, and EnergyWeaponUser claims to have breached Acuity Inc, a federal tech consulting firm,…
[
pic.twitter.com/qGV8IUmkT7
— HackManac (@H4ckManac)
[
April 3, 2024
](https://twitter.com/H4ckManac/status/1775402497768628236?ref_src=twsrc%5Etfw)
The hackers assert that the breach resulted in acquiring full names, emails, office numbers, personal cell numbers, and government, military, and Pentagon email addresses.
⚠️
[
](https://twitter.com/hashtag/BREAKING?src=hash&ref_src=twsrc%5Etfw)
⚠️Allegedly, notorious threat actor IntelBroker, has released National Security Documents and data. Per IntelBroker below..
[
](https://twitter.com/hashtag/Clearnet?src=hash&ref_src=twsrc%5Etfw)
[
](https://twitter.com/hashtag/DarkWebInformer?src=hash&ref_src=twsrc%5Etfw)
[
](https://twitter.com/hashtag/Cyberattack?src=hash&ref_src=twsrc%5Etfw)
[
](https://twitter.com/hashtag/Cybercrime?src=hash&ref_src=twsrc%5Etfw)
[
](https://twitter.com/hashtag/Infosec?src=hash&ref_src=twsrc%5Etfw)
[
](https://twitter.com/hashtag/CTI?src=hash&ref_src=twsrc%5Etfw)
[
](https://twitter.com/hashtag/NSA?src=hash&ref_src=twsrc%5Etfw)
Documents belonging to the Five Eyes Intelligence..
Compromised Data:…
[
pic.twitter.com/I5n41utQN9
— Dark Web Informer (@DarkWebInformer)
[
April 2, 2024
](https://twitter.com/DarkWebInformer/status/1775295354910466200?ref_src=twsrc%5Etfw)
The compromised data also includes classified information and communications between the Five Eyes countries and their allies.
Implications of the Leak
If confirmed, the leak could have significant implications for national security and the operational integrity of the intelligence-sharing network.
The Five Eyes alliance is known for its collaborative intelligence gathering and analysis efforts, playing a pivotal role in global security operations.
At the time of reporting, there has been no official statement from any of the Five Eyes member countries or Acuity Inc. regarding the authenticity of the leaked documents or the extent of the breach.
The silence from official channels has led to speculation and concern among cybersecurity experts and government officials alike.
Cybersecurity agencies are likely to conduct thorough investigations to ascertain the validity of the claims made by the hackers.
The incident underscores the persistent threat cybercriminals pose to national and international security.
`Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free Guide`
The post Hackers Claiming Breach of Five Eyes Intelligence Group (FVEY) Documents appeared first on GBHackers on Security | #1 Globally Trusted Cyber Security News Platform.
posted by pod_feeder
#DataBreach Alert ⚠️
— HackManac (@H4ckManac) April 3, 2024
🇺🇸#USA: Alleged Acuity Inc breach leads to leak of sensitive Five Eyes Intelligence Group (FVEY) documents.
The threat actor group consisting of IntelBroker, Sanggiero, and EnergyWeaponUser claims to have breached Acuity Inc, a federal tech consulting firm,… pic.twitter.com/qGV8IUmkT7

 exported by the payload object file
exported by the payload object file Binary Intelligence technology in action.
Binary Intelligence technology in action..webp)



.webp)
%20(1).webp)




.webp)

 Current DoD and DIB Cybersecurity Efforts
Current DoD and DIB Cybersecurity Efforts DoD DIB Cybersecurity Strategic Alignment
DoD DIB Cybersecurity Strategic Alignment NIST Cybersecurity Framework 2.0 Core
NIST Cybersecurity Framework 2.0 Core

 Playbook for experiment execution (Source – Arxiv)
Playbook for experiment execution (Source – Arxiv)

.webp)