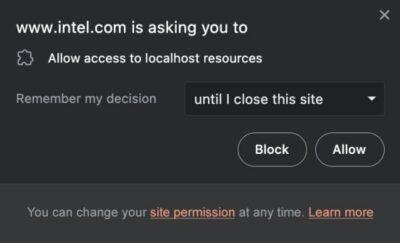
Brave aims to curb the practice of websites that port scan visitors: Great idea, but will a normal user know what ‘localhost resources’ are?
The Brave browser will take action against websites that snoop on visitors by scanning their open Internet ports or accessing other network resources that can expose personal information.
Starting in version 1.54, Brave will automatically block website port scanning, a practice that a surprisingly large number of sites were found engaging in a few years ago.
Some sites use similar tactics in an attempt to fingerprint visitors, so they can be re-identified each time they return, even if they delete browser cookies. By running scripts that access local resources on the visiting devices, the sites can detect unique patterns in a visiting browser.
My only worry is that an average non-tech users is not going to firstly know what localhost resources are, and secondly what impact that may or may not have on their using that site.
Localhost resources are files or resources that are hosted on your local machine. They can be accessed by websites (if not blocked) or applications that are running on your computer, but they are not accessible from the internet.
If you block a website from accessing localhost resources on your computer, it will no longer be able to access files or resources that are hosted on your local machine. This can help to protect your computer from security risks, such as malware or viruses. However, blocking a website from accessing localhost resources may also prevent you from using certain features of the website. For example, if you block a website from accessing your database files, you may not be able to log in to the website or use certain features.
Ultimately, the decision of whether to block a website from accessing localhost resources is up to you. If you are concerned about your security, then blocking websites may be a good option. However, if you need to use certain features of a website, then you may need to allow the website to access your localhost resources.
So the takeaway is: Blocking by default will protect you, but some aspects of a website may break, and if you need to access those for a site you consider safe, then you may have to consider granting access.
See https://arstechnica.com/security/2023/06/brave-will-soon-control-which-sites-can-access-your-local-network-resources/
#Blog, #bravebrowser, #privacy, #technology