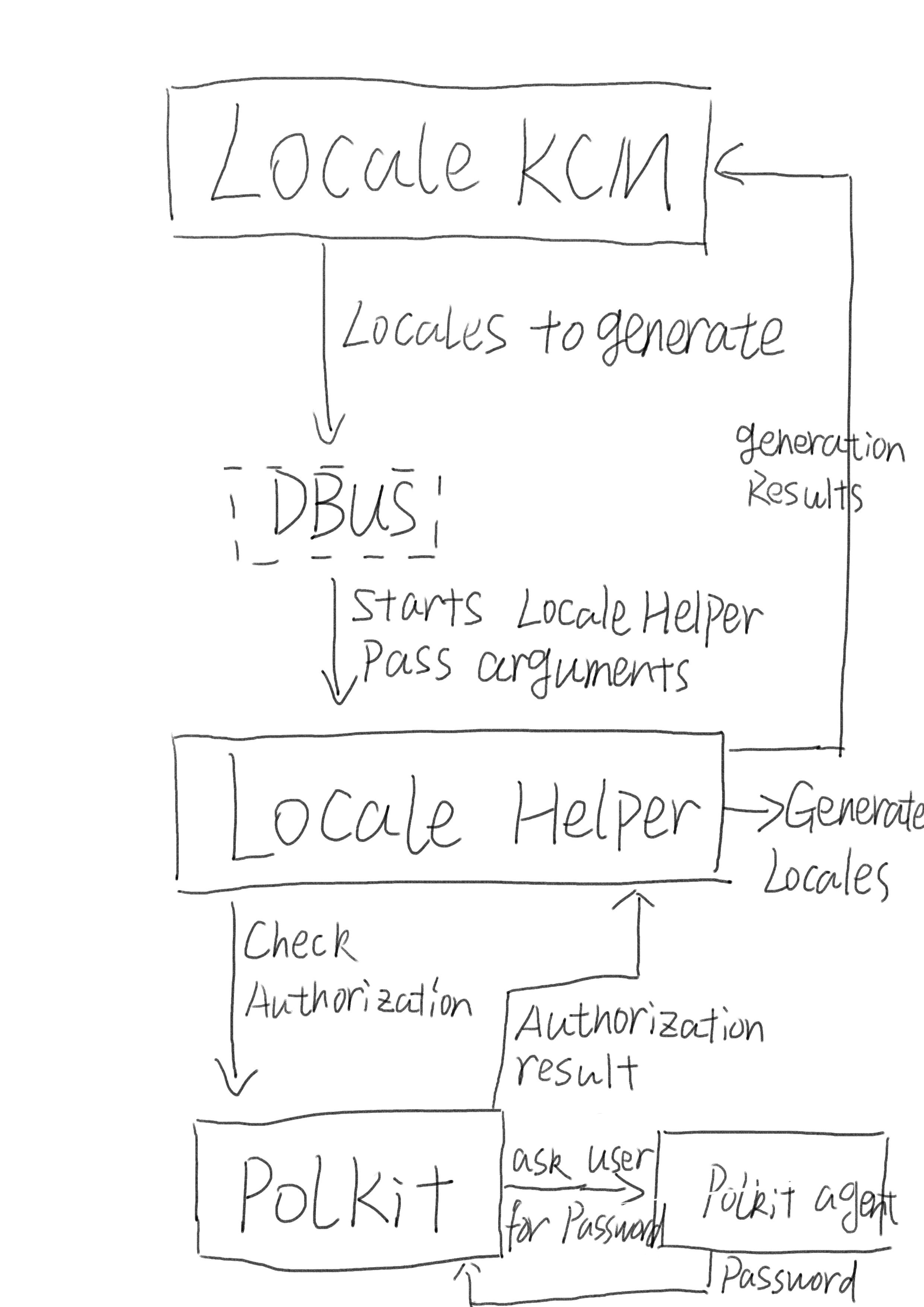
#polkit
"We should try to be empathetic toward software maintainers, including those from #systemd and #polkit , so writing inflammatory posts blaming systemd or its maintainers for polkit does not really help to fix the problems that made this a useful security vulnerability." #twitter is a "thing"? https://ariadne.space/2022/01/27/cve-2021-4034/
Major Bug Grants Root for All Major Linux Distributions
One of the major reasons behind choosing Linux as an operating system is that it's much more secure than Windows. There are plenty of reasons for this including appropriate user permissions, installing software from trusted sources and, of course, the fact that most software for Linux including the Linux kernel itself is open source which allows anyone to review the code for vulnerabilities. This doesn't mean that Linux is perfectly secure though, as researchers recently found a major bug found in most major Linux distributions that allows anyone to run code as the root user.
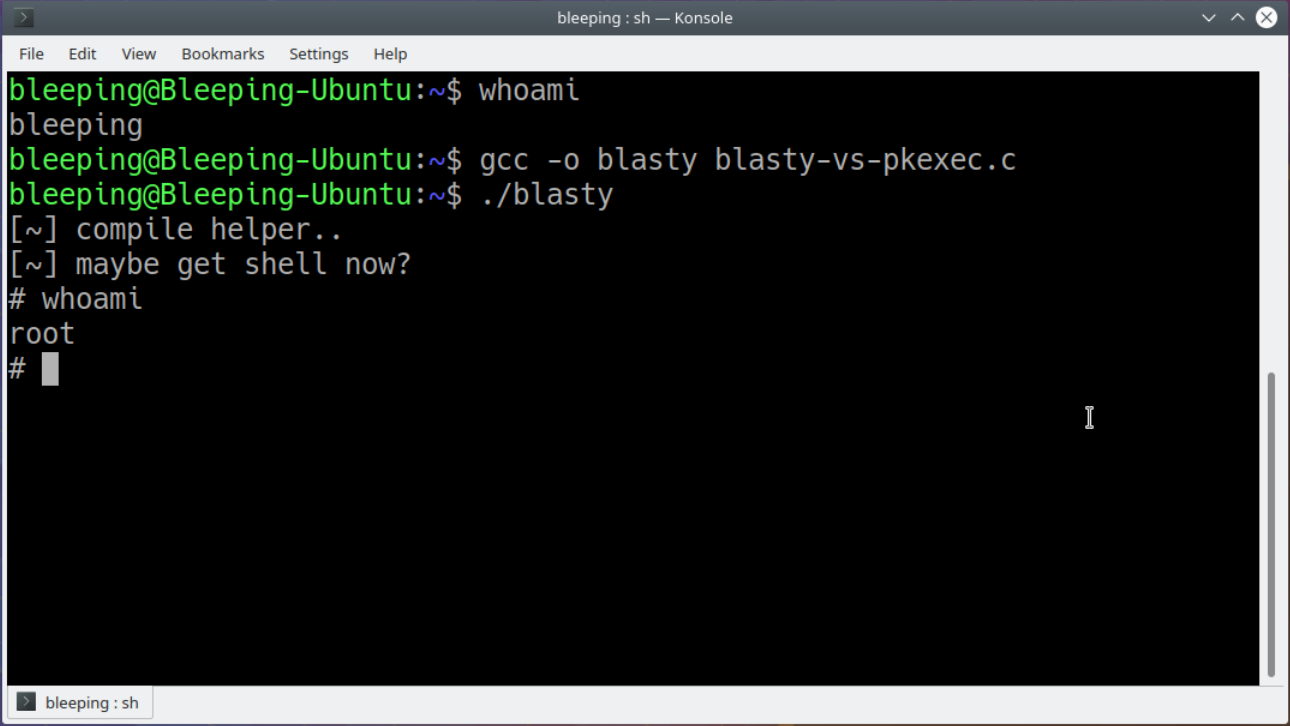
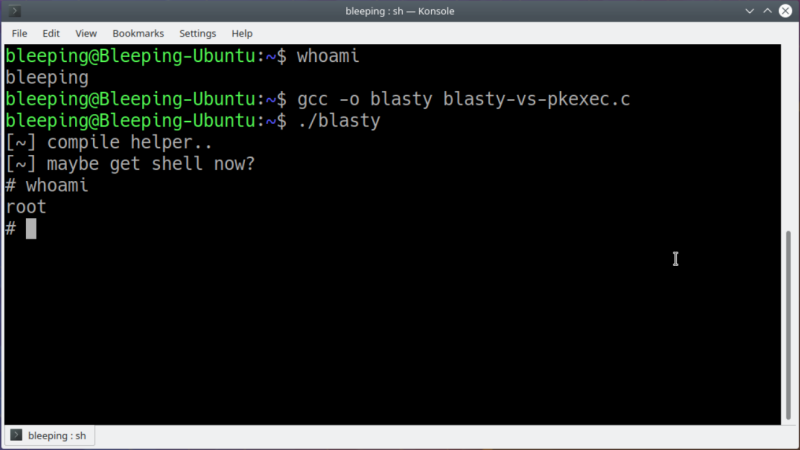
The exploit is a memory corruption vulnerability in Polkit, a framework that handles the privilege level of various system processes. It specifically impacts the program pkexec. With the proof-of-concept exploit (file download warning) in hand, all an attacker needs to do to escalate themselves to root is to compile the program on the computer and run it as the default user. An example is shown by [Jim MacDonald] on Twitter for those not willing to try this on their own machines.
As bad as this sounds, it seems as though all of the major distributions that this impacts have already released updates that patch the issue, including Debian, Ubuntu, Red Hat, Fedora, open SUSE, and Arch. There is also a temporary workaround that removes read/write permission from the pkexec program so it can't run at all. That being said, it might be best to check that your Linux systems are all up-to-date and that no strangers have been typing random commands into the terminal recently.
#linuxhacks #securityhacks #admin #exploit #linux #patch #pkexec #polkit #root #security #update #vulnerability
here's the PwnKit CVE-2021-4034 PoC https://t.co/hIY55cAAzK
— Jim MacDonald (@os2mac) January 26, 2022
#Linux #Server #Problem - #pwnkit: Local Privilege Escalation in #polkit's #pkexec
We discovered a Local Privilege #Escalation (from any user to root) in polkit's pkexec, a SUID-root program that is installed by default on every major Linux #distribution ...
#Workaround if no #patch is available:
chmod 0755 /usr/bin/pkexec