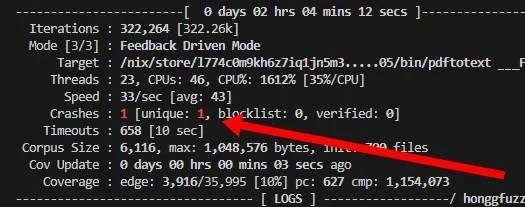
One person like that
#bug
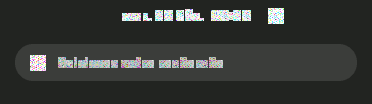
Parfois, à l'allumage, j'obtiens ces hiéroglyphes à la place des caractères et des icônes sur mon bureau Ubuntu... Bizarre...
Si je ferme la session et la rouvre (pas besoin de redémarrer), tout rentre dans l'ordre.
Des idées d'où vient le problème ? J'ai beau chercher, je ne trouve pas 🤔
2 Comments
1 Shares
3 Likes
1 Shares

'Blue Beetle' - I captured this image at the Tirhatuan Park, North Dandenong (Victoria, Australia).
.
.
#beetle #naturephotography #myphoto #bug
7 Likes
#URL File #NTLM Hash Disclosure #Vulnerability (0day) - and Free #Micropatches for it
Source: https://blog.0patch.com/2024/12/url-file-ntlm-hash-disclosure.html
#bug #Patch #Microsoft #Windows #Software #os #cybersecurity #0day #security #news
2 Likes
Copilot let you read the emails of your boss 😱
Source: https://www.businessinsider.com/microsoft-copilot-oversharing-problem-fix-customers-2024-11
Now the software giant is trying to fix the #problem. On Tuesday, #Microsoft released new tools and a guide to help customers mitigate a #Copilot #security issue that inadvertently let employees access sensitive information such as CEO emails and HR documents.
#fail #Software #ai #technology #Windows #news #omg #wtf #privacy #bug
8 Likes
6 Comments
2 Shares
Within this assessment, the red team (also referred to as ‘the team’) gained initial access through a web shell left from a third party’s previous security #assessment.
Source: https://www.cisa.gov/news-events/cybersecurity-advisories/aa24-326a
Today's #security measures therefore tend to reduce security rather than increase it. 🤔😖
#news #Software #vulnerability #bug #fail #cybersecurity #Problem #omg #wtf #web #webshell #internet
One person like that
2 Comments
4 Likes
Why is proprietary #software so bad and full of #vulnerabilities?
The sales department probably doesn't know any better and only has its commission in mind and just sells the software, that's their job. I'm not so sure about the management, whether they are clueless or just think that no matter how bad the software is, we can earn even more money with support contracts. There are certainly a few clueless developers who are kept so busy that they barely manage to complete their tasks but have no time for quality assurance. However, a large part of the developers will realize what is being played and then either change jobs after 2 years if it becomes unbearable or try to justify the quality of the software according to the motto it is a feature and not a bug. Ultimately, the only option left to cybersecurity is to secure vulnerable software with supposedly better security software. Bugs are not fixed unless public pressure is so strong that it is unavoidable and with one fixed bug, three new ones are installed. The supposedly secure security software all too often turns out to be snake oil, which only brings further security risks, which then have to be secured by further security software and you find yourself in a never-ending cascade, which becomes ever more dangerous and expensive but brings no security gain. There is even a technical term for this, called security theater. At the end of the day, all the management wants to say in its press release is that the hackers were diabolical criminals and probably had state support, but that the company had done everything it could to defend itself with the latest security software. The starting position is therefore clear. There is money to be made from security vulnerabilities and proper security means a lot of work. Economic considerations are therefore made here, according to which quality assurance can be saved because the customer can find and report the errors after all.
I'm pretty sure I'm not the smartest or the best developer, but I've figured it out and I'm always surprised that I often meet colleagues who are very confident about cybersecurity in the company because there is security training every year. I don't see any possibility of developing secure software at all under capitalism because profit is always valued higher than security.
#developer #management #economy #capitalism #profit #finance #security #cybersecurity #bug #fail #system #problem #hack #hacker #malware
6 Likes
4 Shares
One person like that

'Imperial Jezabel Butterfly' - I captured this image at my home in Upwey (Victoria, Australia)
.
.
#butterfly #naturephotography #bug #myphoto
6 Likes
#Cisco reports more than 35 #vulnerabilities in #firewall products
Don't forget that you use firewalls to increase #security.
#news #Software #vulnerability #bug #fail #cybersecurity #Problem #fail #qa #economy
3 Likes
1 Shares
https://kopiti.am/@budak/113286594653246847 budak@kopiti.am - oyens
#Singapore #butterfly #schmetterling #orange #insect #bug #animal #wildlife #biodiversity #macro
3 Likes
Trigger Bot 😱🎮
#game #gamer #cheat #software #fail #bug #chat #problem #News
♲ anonymiss - 2024-10-18 09:07:32 GMT
tl;dr: write "trigger bot" in the chat to #exploit #gaming #anticheat #software. This will result in permanently ban for the #gamer 😱- - - - - -
OVERVIEW
Signature scanning is a mechanism implemented by all modern anticheats. When used correctly, it is an effective way to catch and ban cheaters in video games.
Also antiviruses use this technique to catch and identify malware so the method is not new or fundamentally flawed.
The way signature scanning works is that it scans your computers memory for footprint of known cheat software.
This requires that the anticheat devs carefully analyze the cheat and create an UNIQUE signature that is only found in your RAM when the cheat is loaded and NEVER found when the cheat is not loaded.
RICOCHET AND SIGNATURE SCANS
As expected, Ricochet also uses signature scanning as one of its many methods of detecting and banning cheaters.
Earlier this year, when I was tracking memory allocations of their kernel module, I stumbled upon a memory region that caught my attention. Unlike most regions, this one contained
a lot of strings, all of them cheating related. Reversing the structure confirmed my suspicions; it was a list of signatures for a signature scan routine.
THE SIGNATURES
As I said before, anticheats must be extra careful when creating signatures for cheats - a bad signature could lead to innocent players being banned.
Well, without further ado, lets take a look at a few signatures Ricochet has been using:
53 63 72 65 65 6e 73 68 6f 74 20 63 6f 75 6e 74 65 72 (Screenshot counter)
54 72 69 67 67 65 72 20 42 6f 74 (Trigger Bot)
42 00 75 00 62 00 62 00 6c 00 65 00 20 00 45 00 53 00 50 00 (B.u.b.b.l.e. .E.S.P.)
As you can see, Ricochet is a big fan of using plaintext ASCII (and multibyte) strings for their signature scans. What could go wrong?
THE EXPLOIT
So now we know that anyone who has the sequence "Trigger Bot" in their games memory will be flagged as a cheater.
This might sound reasonable at first glance since "Trigger Bot" is a common occurrence in cheat menus. Surely you are using one if this phrase is found from your game, right?
Well, unfortunately for Ricochet, that's not the case. Someone sends a message in game chat, that message will be in your games memory. Someone sends you a friend request - their name will be in your games memory.
When you are playing a game, all the player names in your lobby - guess what? In your games memory.
THE IMPLICATIONS
For quite some time it has been possible to get people permanently banned by sending them a friend request or posting a message ("Nice Trigger Bot dude!") in game chat.
I even heard of someone who made an autohotkey script to spam join Warzone lobbies and post messages in chat to get anyone in the lobby banned who is scanned by Ricochet during the game (couldn't be me, honest).
I am in a position where I can say that several thousand random COD players were banned by this exploit before the streamers began to be targeted. Censor, Parasite - etc and the others were targeted before the big reveal. I planned to target more but it seems when several major streamers are perma banned, Ricochet will turn bans off and investigate. No fun. x)
This is the result of major oversight from the Ricochet team by using improper signatures.
Activision has already started to unban accounts that were banned using this exploit, but this comes with a caveat: also real cheaters who were caught by these signatures will get unbanned. Also Ricochet seems to not understand how many people got pwned by this with their small number claims. x)
You can read their statement here with highly downplays the number of false bans issued - https://x.com/CODUpdates/status/1847001212761350574
#bot #cheat #fail #bug #game #security #Problem #chat #string #trigger #news #cod
tl;dr: write "trigger bot" in the chat to #exploit #gaming #anticheat #software. This will result in permanently ban for the #gamer 😱
OVERVIEW
Signature scanning is a mechanism implemented by all modern anticheats. When used correctly, it is an effective way to catch and ban cheaters in video games.
Also antiviruses use this technique to catch and identify malware so the method is not new or fundamentally flawed.
The way signature scanning works is that it scans your computers memory for footprint of known cheat software.
This requires that the anticheat devs carefully analyze the cheat and create an UNIQUE signature that is only found in your RAM when the cheat is loaded and NEVER found when the cheat is not loaded.
RICOCHET AND SIGNATURE SCANS
As expected, Ricochet also uses signature scanning as one of its many methods of detecting and banning cheaters.
Earlier this year, when I was tracking memory allocations of their kernel module, I stumbled upon a memory region that caught my attention. Unlike most regions, this one contained
a lot of strings, all of them cheating related. Reversing the structure confirmed my suspicions; it was a list of signatures for a signature scan routine.
THE SIGNATURES
As I said before, anticheats must be extra careful when creating signatures for cheats - a bad signature could lead to innocent players being banned.
Well, without further ado, lets take a look at a few signatures Ricochet has been using:
53 63 72 65 65 6e 73 68 6f 74 20 63 6f 75 6e 74 65 72 (Screenshot counter)
54 72 69 67 67 65 72 20 42 6f 74 (Trigger Bot)
42 00 75 00 62 00 62 00 6c 00 65 00 20 00 45 00 53 00 50 00 (B.u.b.b.l.e. .E.S.P.)
As you can see, Ricochet is a big fan of using plaintext ASCII (and multibyte) strings for their signature scans. What could go wrong?
THE EXPLOIT
So now we know that anyone who has the sequence "Trigger Bot" in their games memory will be flagged as a cheater.
This might sound reasonable at first glance since "Trigger Bot" is a common occurrence in cheat menus. Surely you are using one if this phrase is found from your game, right?
Well, unfortunately for Ricochet, that's not the case. Someone sends a message in game chat, that message will be in your games memory. Someone sends you a friend request - their name will be in your games memory.
When you are playing a game, all the player names in your lobby - guess what? In your games memory.
THE IMPLICATIONS
For quite some time it has been possible to get people permanently banned by sending them a friend request or posting a message ("Nice Trigger Bot dude!") in game chat.
I even heard of someone who made an autohotkey script to spam join Warzone lobbies and post messages in chat to get anyone in the lobby banned who is scanned by Ricochet during the game (couldn't be me, honest).
I am in a position where I can say that several thousand random COD players were banned by this exploit before the streamers began to be targeted. Censor, Parasite - etc and the others were targeted before the big reveal. I planned to target more but it seems when several major streamers are perma banned, Ricochet will turn bans off and investigate. No fun. x)
This is the result of major oversight from the Ricochet team by using improper signatures.
Activision has already started to unban accounts that were banned using this exploit, but this comes with a caveat: also real cheaters who were caught by these signatures will get unbanned. Also Ricochet seems to not understand how many people got pwned by this with their small number claims. x)
You can read their statement here with highly downplays the number of false bans issued - https://x.com/CODUpdates/status/1847001212761350574
#bot #cheat #fail #bug #game #security #Problem #chat #string #trigger #news #cod
One person like that
hi, i'm daniel. i'm a 15-year-old with some programming experience and i do a little bug hunting in my free time. here's the insane story of how I found a single bug that affected over half of all Fortune 500 companies:
https://gist.github.com/hackermondev/68ec8ed145fcee49d2f5e2b9d2cf2e52
#Software #bug #backdoor #fail #economy #fail #news #zendesk #cybersecurity #security
3 Likes
3 Comments

08.10.2024 Daten ins Nirwana geschickt
Speichern und löschen sind etwas verschiedenes
Es gibt scheinbar nicht nur "künstliche Intelligenz", sondern beim Microsoft Office 365 auch "künstliche Dummheit". Nutzerinnen und Nutzer des derzeitigen Word (Build 2409) erleben beim Speichern ihrer Dokumente häufig, dass sie sie danach nicht mehr auf der Festplatte vorfinden.
Eine Datei zu erzeugen, sie zu verändern, sie wieder zu speichern oder sie zu löschen sind die grundlegenden Aktionen, die man auf einem Computer vornehmen kann - und eigentlich sind sie seit mehr als 40 Jahren in verschiedenen Vorgängen programmiert.
Trotzdem löscht die oben genannte Word Version Dateien unter Umständen beim Speichern, wenn z.B. die Dateierweiterung in Großschrift geschrieben wird (.DOCX, .RTF)oder das Zeichen # enthält. Das Auftreten des Fehlers wird eventuell dadurch wahrscheinlicher, wenn man Word anschließend statt über "Datei/Schließen" mit dem x oben im Fenster beendet. Die Fehlerursache wird weiter gesucht ...
Einen nicht ganz so gravierenden Fehler erlebten im Frühjahr auch Word NutzerInnen auf Apple Mac. Wenn sie ihr Mac-System mit englischer Sprache, aber deutscher Zahlendarstellung und metrischem System konfiguriert hatten, so hat Word diese Auswahl einfach ignoriert. Wer schon mal mit einer fremdländischen Tastatur arbeiten musste, kann sich leicht vorstellen, wie schnell man dabei verzweifelt.
Mehr dazu bei https://www.heise.de/news/Microsoft-warnt-vor-Word-Fehler-Dateien-geloescht-statt-gespeichert-9964336.html
Kategorie[21]: Unsere Themen in der Presse Short-Link dieser Seite: a-fsa.de/d/3Db
Link zu dieser Seite: https://www.aktion-freiheitstattangst.org/de/articles/8927-20241008-daten-ins-nirwana-geschickt.html
Link im Tor-Netzwerk: http://a6pdp5vmmw4zm5tifrc3qo2pyz7mvnk4zzimpesnckvzinubzmioddad.onion/de/articles/8927-20241008-daten-ins-nirwana-geschickt.html
Tags: #Windows #Microsoft #Office365 #Bug #Speichern #löschen #Tastatur #Zeichensätze #Apple #Mac #Fehler #unbekannt
One person like that
1 Shares
#iOS: A user's saved passwords may be read aloud by #VoiceOver
One person like that
1 Comments
The wrong question ...
#crowdstrike #cybersecurity #microsoft #windows #security #meme #question #economy #software #qa #bug #fail
2 Likes