#tor
● NEWS ● #Tor ☞ Responding to Tor #censorship in #Russia https://blog.torproject.org/tor-censorship-in-russia/ @XRevan86 #ru
Since 2017, someone is running about a thousand — 10% of the total — #Tor servers in an attempt to deanonymize the network" https://www.schneier.com/blog/archives/2021/12/someone-is-running-lots-of-tor-relays.html
Bad Tor Relays
Tracking down the source for this allegation.
It started with a post from Schneier on his blog. I get this as a news feed. https://www.schneier.com/blog/archives/2021/12/someone-is-running-lots-of-tor-relays.html
Schneier links to this. https://therecord.media/a-mysterious-threat-actor-is-running-hundreds-of-malicious-tor-relays/
That led to Nusenu, and just a little more work led to what I think is the ultimate source.
Summary
- A mysterious actor which we gave the code-name KAX17 has been running large fractions of the tor network since 2017, despite multiple attempts to remove them from the network during the past years.
- KAX17 has been running relays in all positions of a tor circuit (guard, middle and exit) across many autonomous systems putting them in a position to de-anonymize some tor users.
- Their actions and motives are not well understood.
- We found strong indicators that a KAX17 linked email address got involved in tor-relays mailing list discussions related to fighting malicious relays.
- Detecting and removing malicious tor relays from the network has become an impractical problem to solve.
- We presented a design and proof of concept implementation towards better self-defense options for tor clients to reduce their risk from malicious relays without requiring their detection.
- Most of the tor network’s exit capacity (>50%) supports that design already. More guard relays adopting the proven domain are needed (currently at around 10%).
#tor #tor-relay #tor-relays #privacy #security #surveillance #spying #tor-network #threat-actor #kax17
#KAX17 threat actor is attempting to deanonymize #Tor users running thousands of rogue relays
Controlling these relays it is possible to see which website the user connects to and, if an insecure connection is used, it is also possible to manipulate traffic. In May 2020, the threat actor managed to control over 380 Tor exit nodes, with a peak on May 22, when he controlled the 23.95% of Tor exit relay.
Workaround: use only trusted exit nodes! -> https://communitydocs.accessnow.org/147-Tor_force_exit_nodes.html
#Anonymous #anonymity #privacy #darknet #NSA #surveillance #browser #internet #security #hack
A mysterious threat actor is running hundreds of malicious Tor relays
- Security researcher claims to have identified threat actor running thousands of malicious servers. - Researchers claims the attacker may be trying to deanonymize and identify Tor users. - Evidence suggests the attacker, tracked as KAX17, is sophisticated and well-resourced. - The Tor Project has removed hundreds of KAX17 servers in October and November 2021.Since at least 2017, a mysterious threat actor has run thousands of malicious servers in entry, middle, and exit positions of the Tor network in what a security researcher has described as an attempt to deanonymize Tor users.
#TOR #internet #security #privacy #TheRecord #tech #software #KAX17 #TorProject
Android application for on-line privacy and security.
InviZible Pro. (Open source)
New version 5.5.0
Keeps privacy, prevents tracking, gets access to blocked and hidden on-line resources.
InviZible Pro uses DNSCrypt, Tor and Purple I2P to achieve maximum security, privacy and comfortable use of the Internet.
DNS is used by most applications to translate domain names into IP addresses to find a remote server with the site that you want to visit. But this communication is not encrypted and can be used by attackers. DNSCrypt encrypts and authenticates DNS traffic, thus preventing DNS tracking and spoofing.
Tor encrypts Internet traffic and hides your actual location. It uses thousands of computers around the world to mask your IP address and prevents activity tracking to preserve your privacy and anonymity. Tor also provides access to onion services. These are sites that are in a completely hidden network without censorship.
The Invisible Internet Project (I2P) is a hidden anonymous network. It includes thousands of computers distributed around the world. Purple I2P encrypts the traffic of your device and sends it through these computers to ensure privacy and anonymity. Start I2P to access i2p sites and other Invisible Internet hidden services.
InviZible Pro can use root, if your device has root privileges, or uses a local VPN to deliver Internet traffic to Tor, DNSCrypt and I2P networks.
- InviZible Pro does not support ipv6 at this time.
Features:
* No root required
* Hides location and IP
* Unblocks the restricted web content
* Prevents tracking
* Allows access to hidden networks
* ARP spoofing detection
* Built-in firewall
* Tethering supported
* No analytics
* No advertisements
* Open source
* Material design theme
Premium feature:
* Automatic Updates – Use the latest versions of InviZible Pro, and its modules such as DNSCrypt , Tor, and Purple I2P.
* Absence of reminder about the need to support the project.
* Priority technical advice.
* Material design night theme
What's New
* Updated DNSCrypt to version 2.1.1.
* Added current connection status to the notification.
* Added tiles to Android Quick Settings for starting/stopping modules.
* Optimized application behavior on unstable networks.
* Optimized battery usage when network connection is unavailable.
* Improved websites handling for the Tor Exclude/Select websites feature.
Please visit the project’s page: https://invizible.net/en
Download from Google Play: https://play.google.com/store/apps/details?id=pan.alexander.tordnscrypt.gp
F-droid: https://apt.izzysoft.de/fdroid/index/apk/pan.alexander.tordnscrypt
Take a look at source code: https://github.com/Gedsh/InviZible
#android #internet #vpn #anonymous #privacy #confidentiality #dnscrypt #tor #i2p #vpn #proxy #invizible #inviziblepro
Frage für einen Freund, wo kann man über #Tor eine E-Mailadresse anlegen ohne diese mit irgendwelchen realen Daten verifizieren zu müssen, so das die Adresse vollkommen anonym ist?
● NEWS ● #PortSwigger #Privacy #Surveillance ☞ #TorProject unveils plans to route device traffic through #Tor anonymity network with new VPN-like service https://portswigger.net/daily-swig/tor-project-unveils-plans-to-route-device-traffic-through-tor-anonymity-network-with-new-vpn-like-service
● NEWS ● #Tor #torproject ☞ Help Censored Users, Run a Tor Bridge https://blog.torproject.org/run-a-bridge-campaign/
● NEWS ● #Tor #torproject ☞ Tor and the humans who use it https://blog.torproject.org/tor-and-the-humans-who-use-it/ they took a bribe from the frauds at #duckduckgo though :/ http://techrights.org/2021/03/15/duckduckgo-in-2021/
● NEWS ● #Tor #torproject ☞ New Release: Tor Browser 11.0.1 https://blog.torproject.org/new-release-tor-browser-1101
New Release: Tor Browser 11.0.1
Tor Browser 11.0.1 is now available from the Tor Browser download page and also from our distribution directory.
This version provides important bug fixes on Windows, MacOS, and Linux, and includes blockchain explorer Blockchair as a search option.
#tor #tor-browser #privacy #surveillance #censorship #security #firefox #firefox-esr #onion-service #onion-services
Portable-Onion-Site Version 1.8 Is Published
This is all you need to create a portable, static, self-hosted, Tor Onion Service Website.
This version just upgrades Tor to version 0.4.6.8.
https://archive.org/details/portable-onion-site
This is a kit, in the form of a signed, but not encrypted, Tar archive that contains all you need to create a portable, static, self-hosted Tor Onion Service website. The webserver is a modified darkhttpd.
Download https://archive.org/download/portable-onion-site/portable-onion-site.gpg and then
- Drag and drop it onto EasyGPG or
- In a terminal window,
gpg portable-onion-site.gpg, and then unpack the resulting Tar archive namedportable-onion-site.
Files
My Public Key https://archive.org/download/portable-onion-site/57b731e9.asc
README https://archive.org/download/portable-onion-site/README
The Whole Package https://archive.org/download/portable-onion-site/portable-onion-site.gpg
#portable-onion-site #tor #onion #website #onion-service #hidden-service #tor-onion-service #tor-hidden-service #censorship #onionland
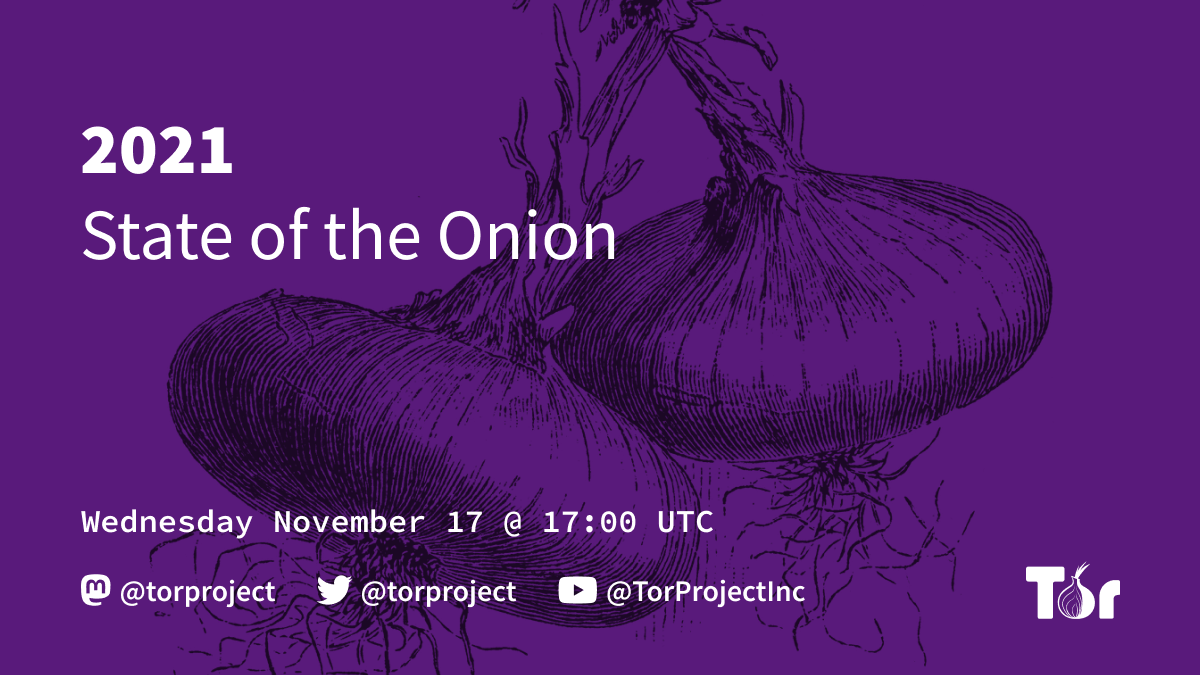
Free and Online ’2021 State of the Onion’ Slated for November 17 - FOSS Force ⚓ https://fossforce.com/2021/11/free-and-online-2021-state-of-the-onion-slated-for-11-17/?utm_source=rss&utm_medium=rss&utm_campaign=free-and-online-2021-state-of-the-onion-slated-for-11-17 ䷉ #fossforce on #tor choosing "YouTube, Facebook, and Twitter" ( #surveillanceCapitalism ) @aral