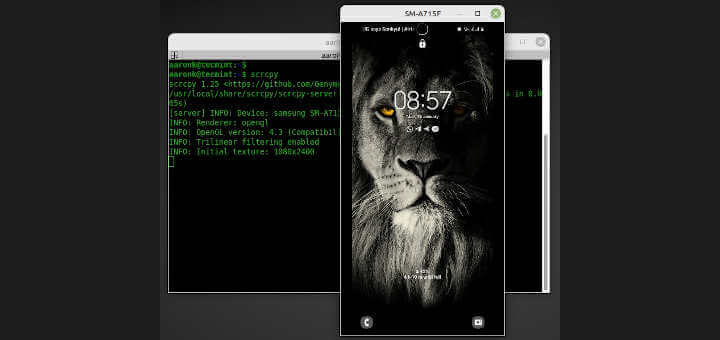
Scrcpy – Display and Control Your Android Device via Linux Desktop
Scrcpy (pronounced “screen copy“) is a free, #open-source, and cross-platform application used to display and control an #Android device from your #Linux desktop computer. It works on Linux, #Windows, and #macOS, and allows you to control a device connected via a #USB or #wirelessly (over TCP/IP).
It features mirroring with Android device screen off, configurable screen display quality, recording, copy and paste in both directions, using an Android device as a webcam (Linux only), physical keyboard and mouse simulation, #OTG mode, and much more.
To use #scrcpy, your Android device must have at least API 21 (Android 5.0), and it must also have #adb (Android Debug Bridge) debugging (USB debugging) enabled. But, it does not require root user access on Linux.