knupSilk - ESTAMPARIA/SERIGRAFIA: Patchs personalizados
https://knupsilk.blogspot.com/2019/11/patchs-personalizados.html
#serigrafia #silkscreen #Personalizadas #EstampasPersonalizadas #patch #banda #postpunk
1 Shares
https://knupsilk.blogspot.com/2019/11/patchs-personalizados.html
#serigrafia #silkscreen #Personalizadas #EstampasPersonalizadas #patch #banda #postpunk
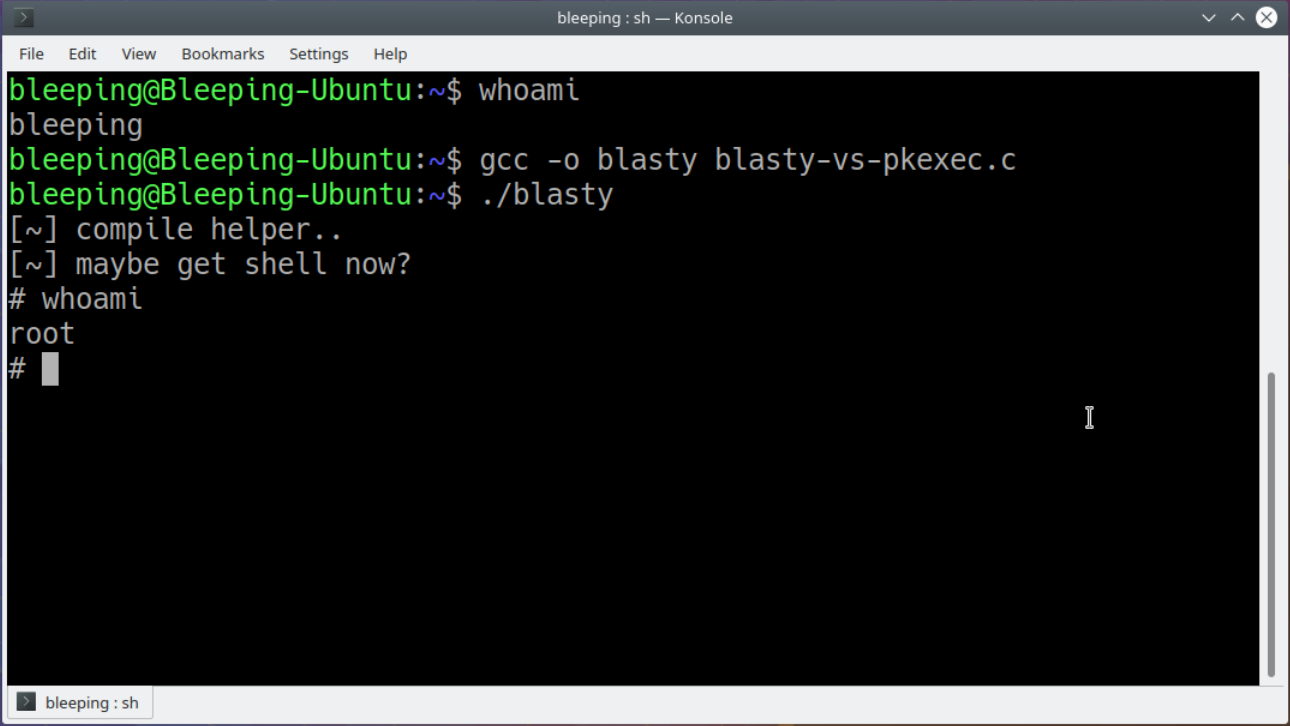
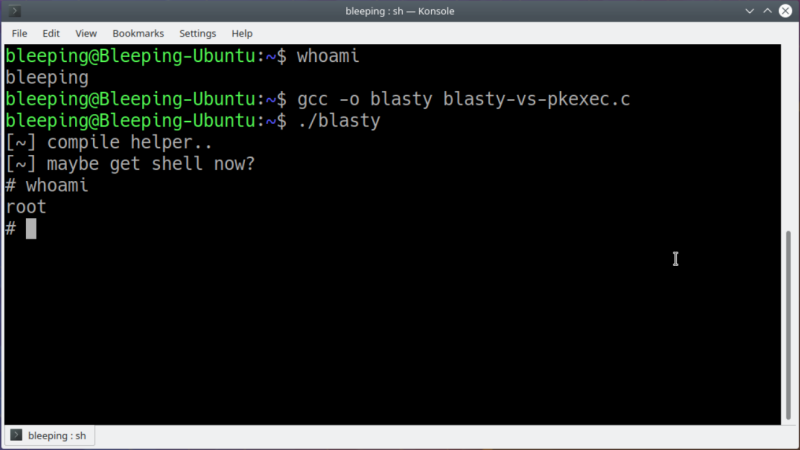
One of the major reasons behind choosing Linux as an operating system is that it's much more secure than Windows. There are plenty of reasons for this including appropriate user permissions, installing software from trusted sources and, of course, the fact that most software for Linux including the Linux kernel itself is open source which allows anyone to review the code for vulnerabilities. This doesn't mean that Linux is perfectly secure though, as researchers recently found a major bug found in most major Linux distributions that allows anyone to run code as the root user.
The exploit is a memory corruption vulnerability in Polkit, a framework that handles the privilege level of various system processes. It specifically impacts the program pkexec. With the proof-of-concept exploit (file download warning) in hand, all an attacker needs to do to escalate themselves to root is to compile the program on the computer and run it as the default user. An example is shown by [Jim MacDonald] on Twitter for those not willing to try this on their own machines.
As bad as this sounds, it seems as though all of the major distributions that this impacts have already released updates that patch the issue, including Debian, Ubuntu, Red Hat, Fedora, open SUSE, and Arch. There is also a temporary workaround that removes read/write permission from the pkexec program so it can't run at all. That being said, it might be best to check that your Linux systems are all up-to-date and that no strangers have been typing random commands into the terminal recently.
#linuxhacks #securityhacks #admin #exploit #linux #patch #pkexec #polkit #root #security #update #vulnerability
here's the PwnKit CVE-2021-4034 PoC https://t.co/hIY55cAAzK
— Jim MacDonald (@os2mac) January 26, 2022
We discovered a Local Privilege #Escalation (from any user to root) in polkit's pkexec, a SUID-root program that is installed by default on every major Linux #distribution ...
#Workaround if no #patch is available:
chmod 0755 /usr/bin/pkexec
source: https://www.howtogeek.com/768727/microsoft-calls-firefoxs-browser-workaround-improper-will-block-it/
The upcoming Windows Update won’t block you from changing the default browser in #Windows 11. The #patch will force links using the microsoft-edge #protocol to always open in #Edge. These are specific links opened through Windows 11, such as those directly from the taskbar’s search feature. Firefox’s workaround and EdgeDeflector made it so these links would still open in your default browser. Microsoft is about to roll out an update that disables this workaround, calling it “improper” on Mozilla’s part

#freedom #openSource #software #economy #win11 #windows11 #news
source: https://news.in-24.com/news/257112.html
More than 50 games do not run properly if you start them on a desktop #PC with a processor from Intel’s Alder Lake-S series such as the Core i9-12900K. The copy protection mechanisms used by the publisher for digital rights management (DRM) are to blame – Intel cites #Denuvo’s software as the most prominent example.
#DRM makes games more expensive, costs electricity and computing power and reduces the gaming experience. It's a no-win #software because it punishes legitimate players.
#gamer #fail #wtf #performance #economy #news #cpu #patch #entertainment
Source: https://www.zdnet.com/article/major-linux-rpm-problem-uncovered/
Why? Because RPM had never properly checked revoked certificate key handling. Specifically, as Linux and lead RPM developer Panu Matilainen explained: "Revocation is one of the many unimplemented things in rpm's #OpenPGP support. In other words, you're not seeing a bug as such; it's just not implemented at all, much like expiration is not."
This is a bad #security #vulnerability but with open source you have the chance to find it and better late than never. You can't say this often enough: "Open source can increase your security but someone with experience has to do a #codereview. If no one checked the code then everything is possible :(
#update #installation #software #opensource #floss #foss #centos #bug #certificate #patch #antipov #suse #redhat #enterprise #signature #fail
#CurveBall #CVE-2020-0601 #microsoft #nsa #https #security #code #exploit #patch #windows
To everyone running a #bitcoin node: #patch your node to avoid double spending #attack:
https://hackernoon.com/bitcoin-core-bug-cve-2018-17144-an-analysis-f80d9d373362
Even weeks after the #vulnerability was closed there are still more than half of the #btc nodes using vulnerable versions (<0.16.3):
https://bitnodes.earn.com/nodes/
surrealist status badge...

#status #badge #surrealism #renemagritte #apple #bowlerhat #hexagon #patch #animatedgif