One person like that
#virtualization
2 Likes
2 Likes
1 Shares
One person like that
One person like that
One person like that
One person like that
Proxmox Backup Server 3.0 mit Debian 12 verfügbar
https://linuxnews.de/proxmox-backup-server-3-0-mit-debian-12-verfuegbar/
#proxmox #virtualization #backups
3 Likes
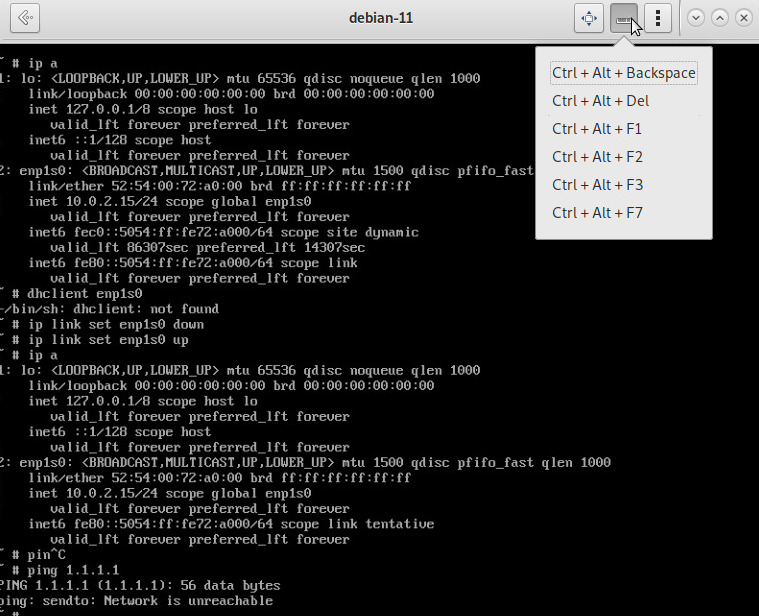
Find the LUKS encryption key in a memory dump file of a Proxmox VM
- Get the partitions from the VM's qcow2 file
ls -alh
-rw-r----- 1 root root 33G Jan 3 19:17 vm-102-disk-0.qcow2
-rw-r----- 1 root root 448M Jan 3 18:05 vm-102-state-luks.rawmodprobe nbd max_part=8
qemu-nbd --connect=/dev/nbd0 vm-102-disk-0.qcow2
fdisk -l
Device Start End Sectors Size Type
/dev/nbd0p1 2048 4095 2048 1M BIOS boot
/dev/nbd0p2 4096 4198399 4194304 2G Linux filesystem
/dev/nbd0p3 4198400 67106815 62908416 30G Linux filesystem
- Find the master key in the memory state dump of the VM with findaes
findaes vm-102-state-luks.raw
Searching vm-102-state-luks.raw
Found AES-256 key schedule at offset 0xb1428dc:
23 02 57 16 22 c1 d4 4f 13 09 00 fa 6c 63 e7 4c 84 91 e1 a3 c5 99 c9 ee 6a 17 cc c7 1f 01 21 f5
Found AES-256 key schedule at offset 0xb142cdc:
22 d2 a6 2e 48 b4 13 d9 4e 1b ed 0c 0b d0 ec 13 e6 39 02 ea 8f b1 dc 70 78 71 89 3f 67 76 a4 2f
Found AES-256 key schedule at offset 0xd97da7a:
38 f3 74 9a 2e 31 92 b0 b4 95 3f 91 c0 cf a7 b9 8b 3e e8 7e bd a0 88 c8 18 4d 8a b0 ee 83 76 66
Found AES-256 key schedule at offset 0xd97dc4a:
38 f3 74 9a 2e 31 92 b0 b4 95 3f 91 c0 cf a7 b9 8b 3e e8 7e bd a0 88 c8 18 4d 8a b0 ee 83 76 66
Found AES-256 key schedule at offset 0xd97deda:
00 01 02 03 04 05 06 07 08 09 0a 0b 0c 0d 0e 0f 10 11 12 13 14 15 16 17 18 19 1a 1b 1c 1d 1e 1f
Found AES-256 key schedule at offset 0xd97e4ba:
d0 b1 91 2f 5b e4 1a c2 7b 96 2f 61 ad bd 25 7d 8a b7 fc 58 f6 99 07 77 dc bd bd b6 fa 18 5a 79
Found AES-256 key schedule at offset 0xd97f69a:
d0 b1 91 2f 5b e4 1a c2 7b 96 2f 61 ad bd 25 7d 8a b7 fc 58 f6 99 07 77 dc bd bd b6 fa 18 5a 79
Found AES-256 key schedule at offset 0xd97f92a:
00 01 02 03 04 05 06 07 08 09 0a 0b 0c 0d 0e 0f 10 11 12 13 14 15 16 17 18 19 1a 1b 1c 1d 1e 1f
Found AES-256 key schedule at offset 0xd9898ac:
31 31 1a 7b 47 92 f6 b8 d5 a4 c2 fb f7 cb a5 ff 5a 28 4d 3b d5 d8 7e 63 fa 8a d0 73 86 79 e3 15
Found AES-256 key schedule at offset 0xd989a7c:
31 31 1a 7b 47 92 f6 b8 d5 a4 c2 fb f7 cb a5 ff 5a 28 4d 3b d5 d8 7e 63 fa 8a d0 73 86 79 e3 15
Found AES-256 key schedule at offset 0xd989d0c:
00 01 02 03 04 05 06 07 08 09 0a 0b 0c 0d 0e 0f 10 11 12 13 14 15 16 17 18 19 1a 1b 1c 1d 1e 1f
- In this case the first 2 matches combined are the master key (2x 256 bits = 512 bits key length)
This may not always be the case. Your best bet is to find two 256 bit keys with successive memory addresses.
- Copy the combined key to a textfile
echo "2302571622c1d44f130900fa6c63e74c8491e1a3c599c9ee6a17ccc71f0121f522d2a62e48b413d94e1bed0c0bd0ec13e63902ea8fb1dc707871893f6776a42f"
> masterkey.txt
- Convert masterkey to binary format
xxd -r -p masterkey.txt masterkey.bin
- Open luks volume
cryptsetup --master-key-file masterkey.bin luksOpen /dev/nbd0p3 myluks
- Open LVM and mount the VM's filesystem
mkdir /mnt/myluks
vgscan --mknodes
Found volume group "ubuntu-vg" using metadata type lvm2mount /dev/mapper/ubuntu--vg-ubuntu--lv /mnt/myluks
ls -alh /mnt/myluks/
total 2,1G
drwxr-xr-x 19 root root 4,0K Jan 3 18:03 .
drwxr-xr-x 6 root root 4,0K Jan 3 19:15 ..
lrwxrwxrwx 1 root root 7 Aug 9 13:53 bin -> usr/bin
drwxr-xr-x 2 root root 4,0K Jan 3 17:57 boot
drwxr-xr-x 4 root root 4,0K Aug 9 13:56 dev
drwxr-xr-x 78 root root 4,0K Jan 3 18:04 etc
drwxr-xr-x 3 root root 4,0K Jan 3 18:04 home
lrwxrwxrwx 1 root root 7 Aug 9 13:53 lib -> usr/lib
lrwxrwxrwx 1 root root 9 Aug 9 13:53 lib32 -> usr/lib32
lrwxrwxrwx 1 root root 9 Aug 9 13:53 lib64 -> usr/lib64
lrwxrwxrwx 1 root root 10 Aug 9 13:53 libx32 -> usr/libx32
drwx------ 2 root root 16K Jan 3 17:57 lost+found
drwxr-xr-x 2 root root 4,0K Aug 9 13:53 media
drwxr-xr-x 2 root root 4,0K Aug 9 13:53 mnt
drwxr-xr-x 2 root root 4,0K Aug 9 13:53 opt
drwxr-xr-x 2 root root 4,0K Apr 18 2022 proc
drwx------ 4 root root 4,0K Jan 3 18:41 root
drwxr-xr-x 9 root root 4,0K Aug 9 13:57 run
lrwxrwxrwx 1 root root 8 Aug 9 13:53 sbin -> usr/sbin
drwxr-xr-x 2 root root 4,0K Jan 3 18:04 snap
drwxr-xr-x 2 root root 4,0K Aug 9 13:53 srv
-rw------- 1 root root 2,0G Jan 3 17:58 swap.img
drwxr-xr-x 2 root root 4,0K Apr 18 2022 sys
drwxrwxrwt 8 root root 4,0K Jan 3 18:59 tmp
drwxr-xr-x 14 root root 4,0K Aug 9 13:53 usr
drwxr-xr-x 13 root root 4,0K Aug 9 13:57 var
#proxmox #luks #encryption #linux #opensource #virtualization #security
6 Likes
1 Comments
Gain unprivileged access to an overlapped directory in Flatpak
Issue
/usr and other hierarchies on the host cannot be accessed from Flatpak, because they conflict with the sandbox. Instead, you are presented with a fake, overlapped filesystem hierarchy. Currently, Flatpak alone has no working options to solve this issue, as configuration overrides have no effect on those special filesystem hierarchies. As Linux does not support directory hard links, this is a serious nuisance!
Solution
Luckily, there is a workaround to safely access the original directory without having root access, if your sysadmin (or you, if you own the system) installed the bindfs package.
The bindfs command uses a FUSE filesystem to mirror the contents of a directory to another directory:
bindfs /overlapped ~/.overlapped
If high performance is needed:
bindfs -o multithreaded /overlapped ~/.overlapped
If security (read-only access) is needed:
bindfs -o ro /overlapped ~/.overlapped
Example
TASK: access the documentation on a Debian system from a Flatpak app.
user@localhost:~$ mkdir .doc
user@localhost:~$ bindfs -o ro,multithreaded /usr/share/doc .doc
user@localhost:~$ ls .doc
…will grant you fast, read-only access to /usr/share/doc by visiting .doc in your user home.
ls .doc will list the contents of /usr/share/doc, while .doc is not a symlink but a simple directory created by you.
You can now eg. use the Flatpak version of Mozilla Firefox to browse file:///home/yourusername/.doc and it will let you read the files in /usr/share/doc, which are normally inaccessible under Flatpak.
Note: this is not an official workaround, I've found by accident. If you know better alternatives please feel free to comment so other users can benefit. Thank you.
Tags: #linux #gnulinux #debian #flatpak #sandbox #virtualization #security #hacking #filesystem #fs #docs #sysadmin #sys #documentation
2 Likes
1 Shares
# if the user wants to be converted from VirtualBox to kvm # 1. first clone the VirtualBox vm into a new vm (to consolidate all snapshots into one vdi # 2. convert file format qemu-img convert -f vdi -O qcow2 virtualbox.vm.vdi[...]
#linux #gnu #gnulinux #opensource #administration #sysops #kvm #virtualization #qemu #gnu-linux
Originally posted at: https://dwaves.de/2022/03/02/gnu-linux-how-to-migrate-vm-from-virtualbox-to-kvm-qemu-convert-virtualbox-vdi-disk-image-to-kvm-qcow2-format/
Sculpt OS release 22.04
https://genode.org/news/sculpt-os-release-22.04
Sculpt OS version 22.04 introduces the concept of service-level sandboxing and features completely new drivers for wireless, graphics, and USB.
#genode #microkernel #osdev #sandboxing #virtualization #security #linux #freebsd #netbsd #openbsd #sel4 #nova #fiasco
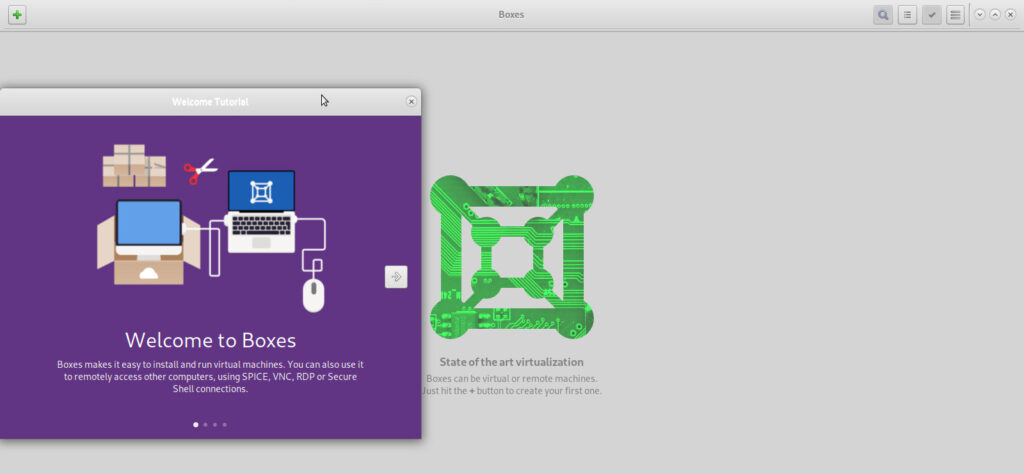
GNU Linux Debian 11 - Gnome Boxes - an Open Source VirtualBox replacement?
In search for alternatives, decided to test drive “gnome boxes“, which is said, to be an easy-going gui for the libvirt qemu virtualization system.
<span style="color: #00ffff;">lsb_release -d</span>; # tested on
Description: Debian GNU/Linux 11 (bullseye)
<span style="color: #00ffff;">su - root
apt update
</span># with MATE Desktop (Gnome2) it's actually only 175MBytes that needs to be downloaded<span style="color: #00ffff;">
apt install gnome-boxes
apt show gnome-boxes</span>
Package: gnome-boxes
Version: 3.38.2-1
Priority: optional
Section: gnome
Maintainer: Debian GNOME Maintainers <pkg-gnome-maintainers@lists.alioth.debian.org>
Installed-Size: 7,140 kB
Depends: genisoimage, libosinfo-bin, libvirt-daemon, tracker (>= 2.0), dconf-gsettings-backend | gsettings-backend, libarchive13 (>= 3.1.2), libc6 (>= 2.7), libcairo2 (>= 1.6.0), libfreerdp2-2 (>= 2.0.0~git20160317.1.75ae3f5+dfsg1), libgdk-pixbuf-2.0-0 (>= 2.25.2) | libgdk-pixbuf2.0-0 (>= 2.25.2), libglib2.0-0 (>= 2.52.0), libgtk-3-0 (>= 3.22.20), libgtk-vnc-2.0-0 (>= 0.5.1), libgtksourceview-4-0 (>= 2.91.4), libgudev-1.0-0 (>= 165), libhandy-0.0-0 (>= 0.0.11), libosinfo-1.0-0 (>= 1.4.0~), libpango-1.0-0 (>= 1.14.0), libsecret-1-0 (>= 0.7), libsoup2.4-1 (>= 2.44), libspice-client-glib-2.0-8 (>= 0.35), libspice-client-gtk-3.0-5 (>= 0.32), libtracker-sparql-2.0-0 (>= 0.10.0), libusb-1.0-0 (>= 2:1.0.8), libvirt-glib-1.0-0 (>= 3.0.0), libvte-2.91-0 (>= 0.40.2), libwebkit2gtk-4.0-37 (>= 2.26), libwinpr2-2 (>= 2.0.0~git20160317.1.75ae3f5+dfsg1), libxml2 (>= 2.7.8)
Recommends: qemu-system-x86
Breaks: libspice-server1 (<< 0.12.5-1.1~)
Homepage: <a href="https://wiki.gnome.org/Apps/Boxes">https://wiki.gnome.org/Apps/Boxes</a>
Tag: admin::virtualization, hardware::emulation, implemented-in::python,
implemented-in::vala, interface::graphical, interface::x11,
role::program, scope::application, suite::gnome, suite::openstack,
system::cloud, system::virtual, uitoolkit::gtk, use::simulating,
use::viewing, x11::application
Download-Size: 1,085 kB
APT-Manual-Installed: yes
APT-Sources: <a href="http://ftp.halifax.rwth-aachen.de/debian">http://ftp.halifax.rwth-aachen.de/debian</a> bullseye/main amd64 Packages
Description: Simple GNOME app to access remote or virtual systems
GNOME Boxes is a desktop client to view or use local virtual machines,
remote physical machines, or remote virtual machines.
Boxes is intentionally simple and easy to use.
Hardware virtualization is required to use local virtual machines.
as minimalistic as the description is the gui:
indeed nothing against a bit of gui minimalism…
kvm is developed by Redhat… that’s why it is right there on top… but there is more for “easy” or “instant” install…
would have been nice, if the disk size can be directly entered in numbers as well…
also a checkbox for “thin provisioning” would have been nice
but it definately works
the vm properties tab, might be a bit too minimalistic… when changing vm settings afterwards, the user will have to rely on the user’s xml editing skillz ;-p
this isa nicely done overview screen… showing real time thumbnails of the all vm’s current desktop…
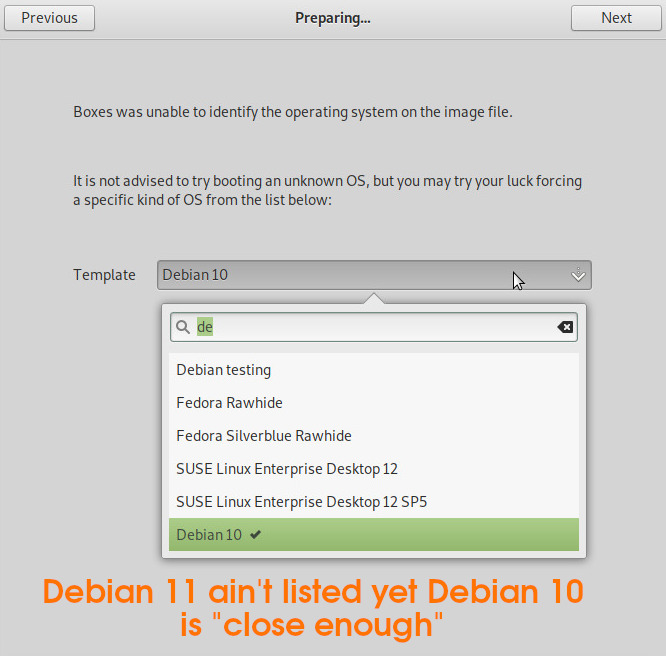
when almost finished installing Debian 11… gnome boxes skips the “where to install grub” screen and reports “debian 11 is ready to use”
but it won’t boot X-D
just in case if the cursor is “stuck” it can be released by hitting Ctrl+Alt
the gui minimalism is a nice try, but gnome-boxes got some quality issues there, not ready for use with Debian, not ready to replace redhat’s kvm’s excellent virtmanager, which works flawless under GNU Linux Debian and has way more settings to modify vms
#linux #gnu #gnulinux #opensource #administration #sysops #gnome #boxes #virtualbox #kvm #virtual #vm #virtualization #qemu
Originally posted at: https://dwaves.de/2022/05/10/gnu-linux-debian-11-gnome-boxes-an-open-source-virtualbox-replacement/
One person like that
1 Comments
- first off the praise:
- now the critique:
- it does not feel very user friendly X-D
- why is thin provisioning not the disk-saving default option?
- or at least should be possible for the user to select this option in virt-manager
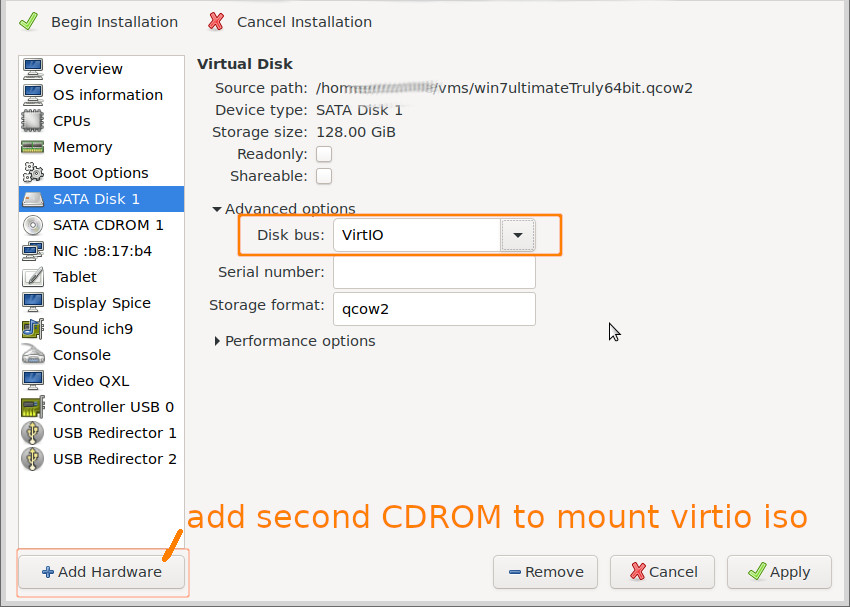
- do not drop windows 7 support just yet… many virtualization systems such as VirtualBox are actually intended to run “outdated” OS on newer hardware for the sake of getting programs to run, that are incompatible with recent OS.
- please double check that virtio 64Bit drivers actually work under win 7 64bit (home, pro and ultimate)
<span style="color: #00ffff;">
hostnamectl</span>; # host is
Chassis: desktop
Operating System: Debian GNU/Linux 10 (buster)
Kernel: Linux 4.19.0-17-amd64
Architecture: x86-64
# hardware used
<span style="color: #00ffff;">cat /proc/cpuinfo |head</span>
processor : 0
vendor_id : AuthenticAMD
cpu family : 23
model : 113
model name : AMD Ryzen 5 3600 6-Core Processor
stepping : 0
microcode : 0x8701021
cpu MHz : 1870.721
cache size : 512 KB
physical id : 0
<span style="color: #00ffff;">dmidecode | less</span>
Manufacturer: ASUSTeK COMPUTER INC.
Product Name: Pro WS 565-ACE
Version: Rev X.0x
<span style="color: #00ffff;">qemu-system-x86_64 --version</span>
QEMU emulator version 3.1.0 (Debian 1:3.1+dfsg-8+deb10u8)
Copyright (c) 2003-2018 Fabrice Bellard and the QEMU Project developers
# installed software
<span style="color: #00ffff;">dpkg -l|grep virt</span>
ii gir1.2-libvirt-glib-1.0:amd64 1.0.0-1 amd64 GObject introspection files for the libvirt-glib library
ii libgovirt-common 0.3.4-3.1 all GObject-based library to access oVirt REST API (common files)
ii libgovirt2:amd64 0.3.4-3.1 amd64 GObject-based library to access oVirt REST API
ii libvirglrenderer0:amd64 0.7.0-2 amd64 virtual GPU for KVM virtualization
ii libvirt-clients 5.0.0-4+deb10u1 amd64 Programs for the libvirt library
ii libvirt-daemon 5.0.0-4+deb10u1 amd64 Virtualization daemon
ii libvirt-daemon-system 5.0.0-4+deb10u1 amd64 Libvirt daemon configuration files
ii libvirt-glib-1.0-0:amd64 1.0.0-1 amd64 libvirt GLib and GObject mapping library
ii libvirt0:amd64 5.0.0-4+deb10u1 amd64 library for interfacing with different virtualization systems
ii ovmf 0~20181115.85588389-3+deb10u3 all UEFI firmware for 64-bit x86 virtual machines
ii python3-libvirt 5.0.0-1 amd64 libvirt Python 3 bindings
ii qemu-kvm 1:3.1+dfsg-8+deb10u8 amd64 QEMU Full virtualization on x86 hardware
ii virt-manager 1:2.0.0-3 all desktop application for managing virtual machines
ii virt-viewer 7.0-2 amd64 Displaying the graphical console of a virtual machine
ii virtinst 1:2.0.0-3 all Programs to create and clone virtual machines
something is pretty off here.
it all starts of with virsh-manager not detect Windows 7 iso correctly, and having to chose it manually enabling the legacy checkbox.
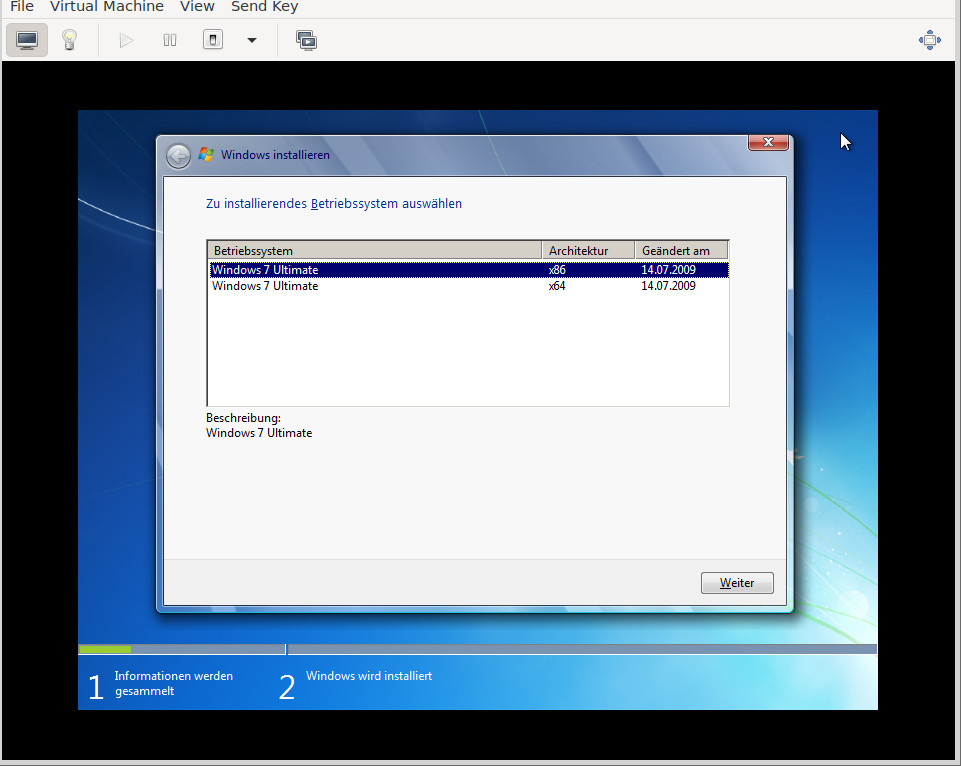
the idea was to install:
- Windows 7 64Bit Ultimate
- SP1
- - Windows 7 Service Pack 1 (32 Bit)
- Windows 7 & Server 2008 R2 Service Pack 1 (64 Bit)
- Windows 7 & Server 2008 R2 Service Pack 1 (ISO-Image, enthält 32-, 64-Bit und IA64)
- - Windows 7 Service Pack 1 (32 Bit)
- WinFuture Update pack
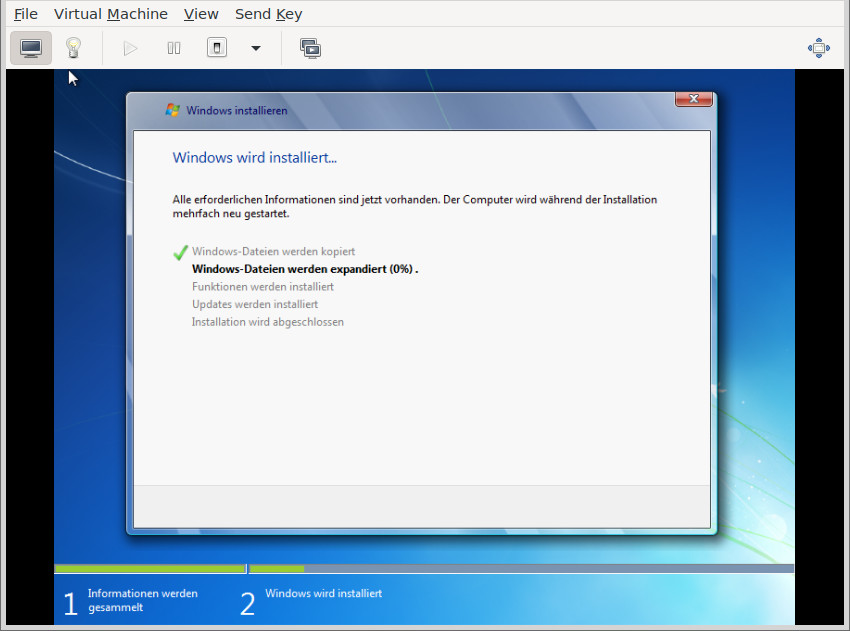
actually managed to install it once… but when trying to install the updates, things became very very slow aka stuck.
next try… it won’t go over this screen: “windows files are being extracted 0%” just sits there doing nothing.
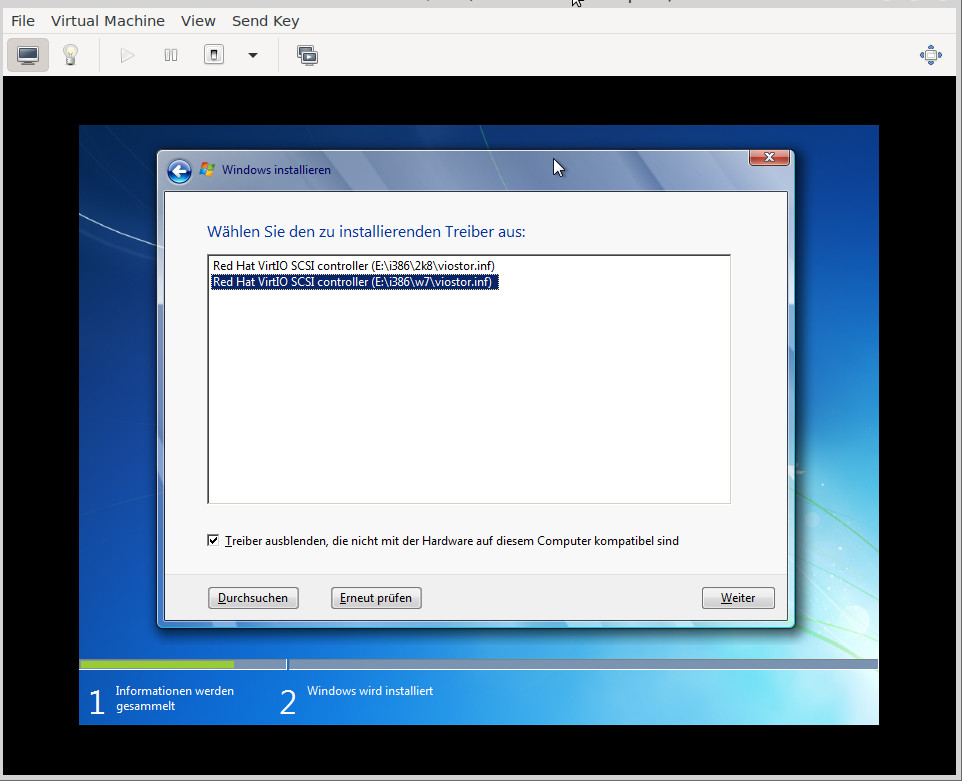
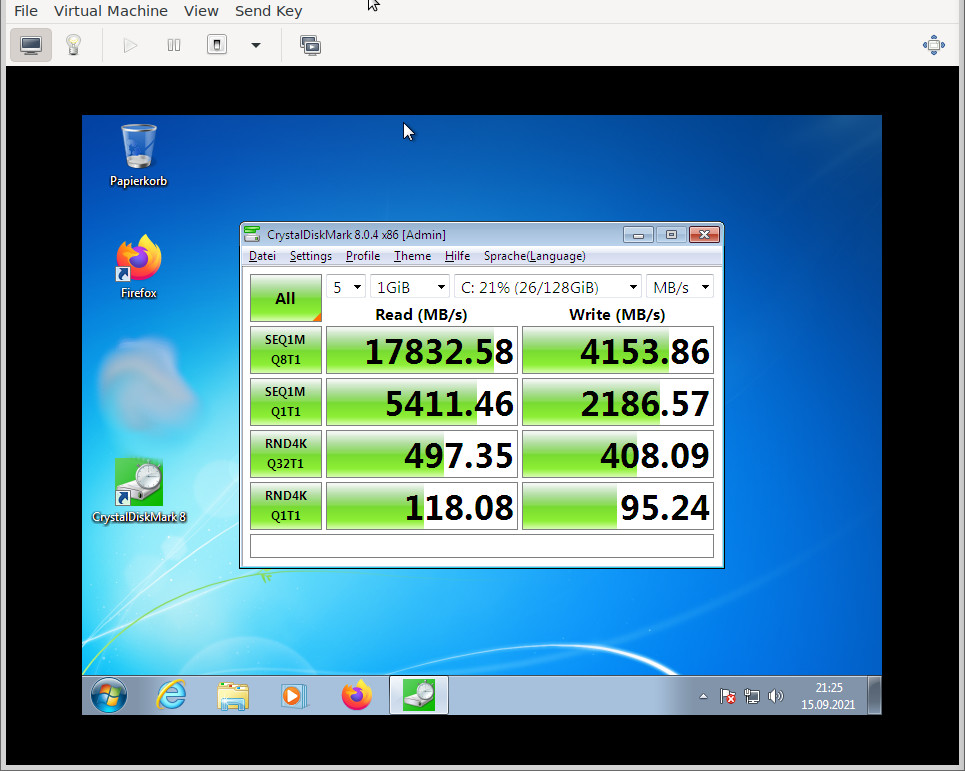
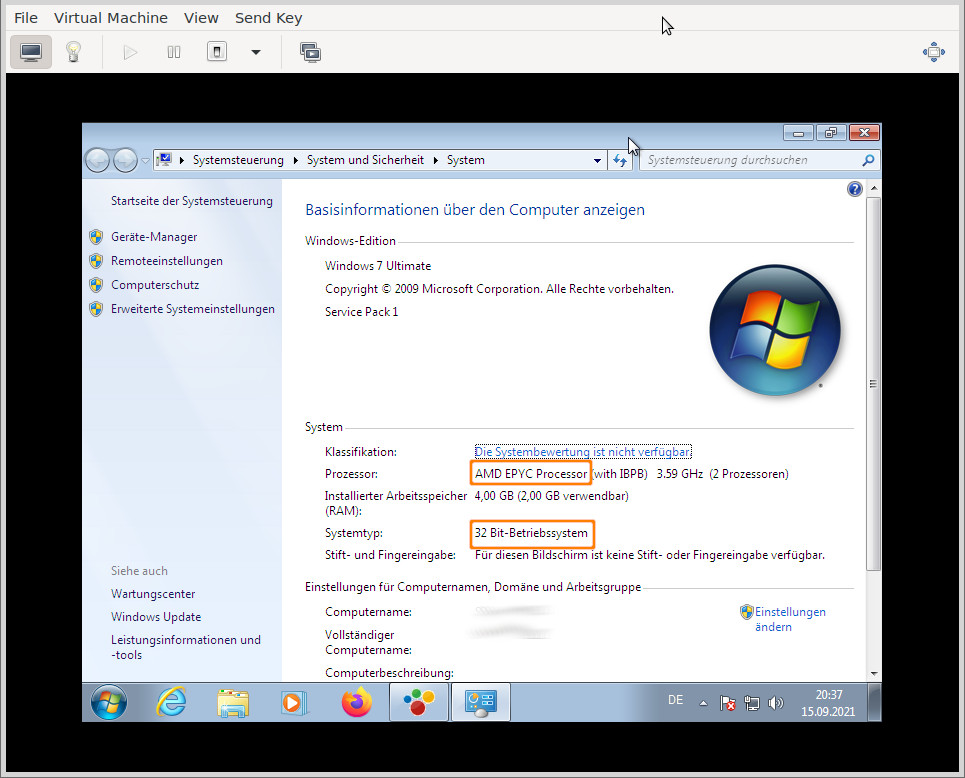
what worked: virtio & 32Bit
the only success that can be reported is for 32Bit! (virtio-win-0.1.173.iso being the last version supporting Windows 7)
now the performance is pretty decent X-D (of course this is all RAM cached stuff)
no chance to select any 64Bit drivers!? in any virtio iso!?
#linux #gnu #gnulinux #opensource #administration #sysops #windows #kvm #qemu #debian #virtualization #virtio
Originally posted at: https://dwaves.de/2021/09/15/gnu-linux-debian-10-kvm-qemu-virtualization-host-sata-disk-access-performance-problems-with-windows-7-64bit-vm-guest-only-32bit-works-with-virtio-drivers-crystal-disk-benchmark-looking-good/
#Virtualization on PC, Explained for Beginners with Practical Use Cases • 𝗧𝘂𝘅 𝗠𝗮𝗰𝗵𝗶𝗻𝗲𝘀 ⇨ http://www.tuxmachines.org/node/154113 #GNU #Linux #TuxMachines
#Virtualization : QEMU , Virtuozzo, and OpenVZ • 𝗧𝘂𝘅 𝗠𝗮𝗰𝗵𝗶𝗻𝗲𝘀 ⇨ http://www.tuxmachines.org/node/153682 #GNU #Linux #TuxMachines
#QEMU 6.1 Is On The Way For The Open-Source Linux #Virtualization Stack - Phoronix ⚓ https://www.phoronix.com/scan.php?page=news_item&px=QEMU-6.1-rc0-Released ䷉ #Phoronix #Kernel #Linux