3 Likes
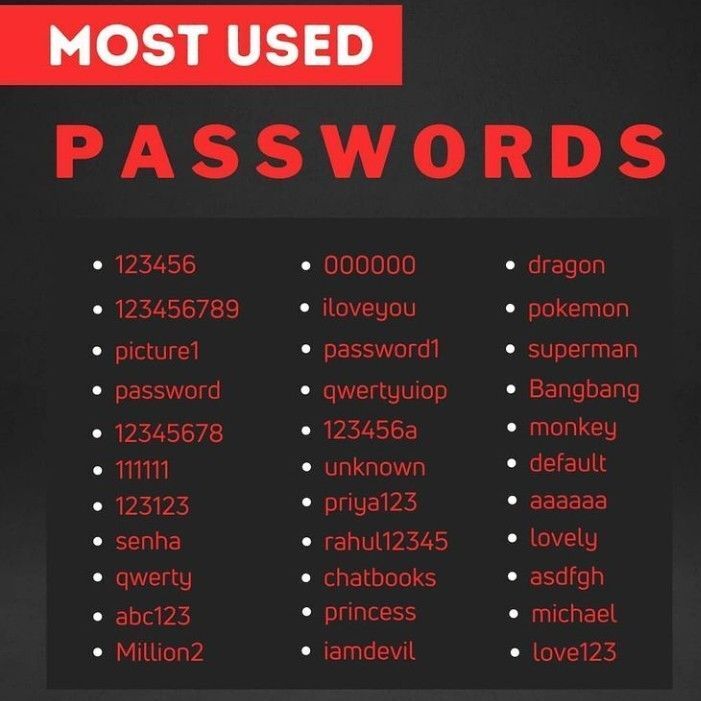
#password

What took them so long? New York Times, Guardian finally call for Assange’s freedom
https://www.wsws.org/en/articles/2022/11/29/pers-n29.html
The editors of the #Guardian, #NYTimes etc. finally speak up for #JulianAssange -- weasel words and 10 years late. Ten years after the Guardian made #public #WikiLeaks' #secret #password and launched a #campaign of #vilification against a #truthteller. The #movement in #Assange’s #defense must be based on the #international #working-class, a #force more #powerful than all of the #governments, #intelligence-agencies and #corporations combined.
#whattookthemsolong #media #biden #dropthecharges #journalism #freepress #publishers #journalismisnotacrime #freeassange #freespeech #weareallassange #publishingisnotacrime
9 Likes
1 Shares
4 Likes
Becoming #Anonymous: The Complete #Guide To Maximum #Security #Online
Attention! Highest danger level! The following link leads you directly to the #YouTube data mafia. It is strongly recommended to use this link only with appropriate security protection: https://www.youtube.com/watch?v=4Z7H5tXqMGo
Alternative: https://yewtu.be/watch?v=4Z7H5tXqMGo
Choose another instance: https://redirect.invidious.io/watch?v=4Z7H5tXqMGo
#password #web #internet #www #isp #privacy #surveillance #browser #tracking #messenger #tor #fdroid
6 Likes
3 Comments
1 Shares
Ad-tech firms grab #email addresses from forms before they're even submitted
Source: https://www.theregister.com/2022/05/16/ad_companies_data/
And many companies involved in data gathering and advertising appear to believe that they're entitled to grab the information website visitors enter into forms with scripts before the #submit button has been pressed.
...
"Furthermore, we find incidental #password collection on 52 websites by third-party session replay scripts," the researchers say.
#security #privacy #fail #surveillance #internet #technology #web #html #www #economy #news #problem
2 Likes
1 Comments
The Force won’t save you from these breached #passwords #StarWarsDay
source: https://specopssoft.com/blog/the-force-wont-save-you-breached-passwords-starwarsday/
Top 20 Star Wars themed passwords found in breached lists:
yoda
starwars
ewok
hansolo
darthvader
bobafett
darthmaul
grogu
obiwankenobi
lukeskywalker
macewindu
anewhope
plokoon
mandalorian
princessleia
kyloren
kuiil
iamyourfather
quigonjinn
rogueone
#password #security #starWars #fans #fail #problem #login #news
One person like that
5 Comments

Wifi and passwords
(the password is #XavlegbmaofffassssitimiwoamndutroabcwapwaeiippohfffX )
#wif #password #goregrind #gore #metal #albumcover
2 Likes
1 Shares
How I Cracked #CONTI #Ransomware Group’s Leaked Source Code #ZIP File
Grab some known plaintext from the second, and you can crack the first with #bkcrack.
#news #password #hack #hacker #security #encryption #software #knowledge
2 Likes
How an 8 year old exploited #Zoom to get a time off from home schooling
source: https://twitter.com/mfpiccolo/status/1360685864100237318
After hours on the phone with Zoom tech support the techs are completely stumped. They say that the account was locked at some point but my sister knows there has been hundreds of login attempts from multiple locations so that makes sense.
...
The more times you do this, the longer the wait period for you to get back into Zoom. She also noticed that the error that is presented to a user when they are locked is “Incorrect password” and not “your account has been locked”. My niece found the #exploit and combined it with her cute 8 year old face, a face that never could tell a lie much less pull off an elaborate scheme to trick no less that 8 adults for 3 weeks straight.
#school #education #technology #internet #support #children #hacker #news #password #login #error
The grifter: My 8 year old niece
— Mike Piccolo (@mfpiccolo) February 13, 2021
The prize: Playing virtual hooky permanently (School Zoom calls)
The marks: My sister, my brother in law, the teacher, the school’s computer teacher, the principle and Zoom's support team
The con: How she pulled it off… thread pic.twitter.com/cdz3SRhRu9
7 Likes
2 Comments
3 Shares
4 Likes
2 Comments
10 Likes
1 Comments
3 Shares
16 Likes
1 Comments
1 Shares
#China accused of foreign interference after Prime Minister Scott #Morrison's #WeChat #account #hijacked and renamed
"WeChat is owned by #Tencent, which is one of the most closely controlled, theoretically private companies in China," he told Sky News
"It censors the platform all over the world. It uses the platform to surveil and monitor the overseas Chinese community.
"It is very clearly a Chinese government action in my view."
Or his #password was too poorly chosen...
#news #surveillance #fail #communication #problem #app #hack #cybercrime #privacy #Australia #politics
2 Likes
10 Comments
How to send a #password securely over an unsecured #connection
A relatively common task for me as a hacktivist is to set up secure #communication channels for technologically innocent newbies. I could of course explain to them how #GPG works, but this often fails due to the lack of will to understand and download and install the programs. Very often I use #XMPP server inside the #onion network (TOR) for #communication. The target must install the Tor #browser for this and can then use an XMPP web client. I can set all that up. The only problem is how do I send the authentication data for the XMPP access securely over an unencrypted connection?
I use #PrivateBin for this #problem: https://privatebin.info
PrivateBin is a #PastBin with encryption and burn after reading features. I post a message on PrivateBin with all the information and burn after reading. The message is encrypted and can only be decrypted with a parameter send together with the URI. The URI can look like this:
https://privatebin.net/?55ac2c8792cb12b9#3fQw1R8SAAQUUGsoa7nDdkYwq34Pzw6GQeSA56v5nusq
If the user can log in, then the authentication data has reached him without being compromised. After that, everything else can be discussed over an encrypted connection. If the user cannot log in, the data may have been intercepted. If you operate the PrivateBin server yourself, you can see which IP has accessed it. You should change the XMPP server and create new authentication in this case.
It can happen that with a weak internet connection the page cannot be loaded completely and when you press reload, of course it doesn't work because the page only works once due to the "burn after reading". Then you have to send the whole thing again with a newly generated URI. But if this does not work several times you should be very careful. Secret service agents like to play the fool in order to tempt you to use unsecured communication channels that are easier for them to wiretap.
#wisdom #knowledge #internet #instruction #security #privacy #surveillance #encryption
5 Likes
3 Comments
1 Shares
4 Likes
6 Comments
1 Shares
Seahorse: Manage Your Passwords & Encryption Keys in Linux
A simple open-source password and encryption key manager app, let’s explore what it has to offer and how you can get it installed. #linux #FOSS #password manager
Seahorse: Manage Your Passwords & Encryption Keys in Linux - It's FOSS
One person like that
America's secret #terrorist #watchlist exposed on the #web without a #password
Source: https://www.linkedin.com/pulse/americas-secret-terrorist-watchlist-exposed-web-report-diachenko/
The exposed server was taken down about three weeks later
3 Likes
1 Shares
One person like that
We all need a password manager right now but for a completely different reason than you think (no clickbait)
TL;DR: Give black hat hackers and #intelligence agencies something to do by creating an encrypted #fake #password #manager file on your system.
When criminal forces like the #NSA hack your system, they are always on the hunt for exploitable files. A list of all your accounts and passwords is of course the jackpot. That is why such files obviously belong on an external data drive that is not constantly connected to the #Internet. However, so that these bandits are not sad, you can create a fake file for them, called a #honeypot.
Such a honeypot has several advantages. If you are in a hurry, you may grab the pot and don't look at the rest so deeply. Decrypting the password file hogs resources that the NSA would otherwise use to declare environmental activists as environmental terrorists.
When choosing a program, it is not so important which one you use (of course I would be happy if you use free #software). The created file should only be encrypted and password protected. Actually, all current password managers fulfill this requirement.

Which password manager do you use? What is your favorite password? Make sure to write it in the comments and leave a like if you have enjoyed the post. Don't forget to subscribe to my channel to avoid missing any more valuable posts from me ...
#knowledge #security #advice #protection #hack #hacker #surveillance #privacy #encryption
4 Likes
29 Comments
1 Shares