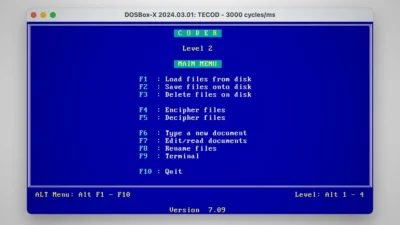
Secret crypto code that helped end apartheid has been cracked and open-sourced
Operation Vula was a mission to infiltrate key leaders such as Mac Maharaj and Charles Nqakula into South Africa while ensuring good lines of communication between them and the ANC’s headquarters-in-exile in Lusaka, Zambia.
“Even in those days, 25 years before Edward Snowden, there was talk about ‘backdoors’ in encryption software,” Jenkin previously told MyBroadband.
Encrypted messages were transmitted into a signal that could be played over a regular telephone call and recorded. This allowed operatives to easily receive messages via public telephones.
The recorded message could then be played back into a computer via a modem and decrypted.
Interesting history and because this was before the availability of the Internet everywhere, more legacy mode transmissions were required.
Why the code has remained hidden for so long, was that it was stored in an encrypted zip file, and if you forget your password, you can’t open it (a valuable lesson for anyone wanting to be super-secret, is don’t forget your password, 10 years later).
And although there is a known vulnerability with the ZipCrypto scheme used, it was not as simple as just running bkcrack.
See mybroadband.co.za/news/softwar…
#Blog, #apartheid, #encryption, #privacy, #southafrica, #technology