1 Shares
#privacy
2 Likes
Home Assistant’s new hardware voice assistant answers to ‘Hey Jarvis’ and can work offline

There’s a new voice assistant in town, and this one can work locally in your home without phoning home to its corporate overloads. This week, the popular hobbyist smart home platform Home Assistant officially launched its first voice assistant hardware — Home Assistant Voice Preview Edition.
Built for the open-source smart home platform, Voice PE costs $59 and brings a locally controlled, privacy-focused voice assistant to Home Assistant in a plug-and-play package. Once connected to Home Assistant, you can use voice to control any connected device, with commands such as “Turn on the living room lights,” “Lock all the doors,” “Create a timer for 5 minutes,” and many more.
There have been other solutions before, but they were not so reliable, and of course the Google or Amazon based ones require the cloud access of these companies, and many do not like to have that channel open.
This is a hardware device (that does look pretty good) and seems to be pretty versatile. I think it could be well worth it, as long as it will get ongoing updates and not be replaced with some new model in the short term. Despite that, seeing it works fully offline, you should at least find it won’t ever be bricked or turned into a paper weight.
See theverge.com/2024/12/19/243251…
#Blog, #homeassistant, #privacy, #technology
One person like that
1 Shares
2 Likes
1 Shares
Jean GautierLa citation du soir :C'est toujours l'oppresseur, non l'opprimé qui détermine la forme de lutte. Si l'oppresseur utilise la violence, l'opprimé n'aura pas d'autre choix que de répondre par la violence. Dans notre cas ce n'était qu'une forme de légitime défense.
#Nelson-Mandela
4 h
/e/OS - deGoogled mobile OS @e_mydata@mastodon.social
✨ Discover our new /e/OS Installer (Beta)! ✨
Say goodbye to complexity—our new Installer makes it easier than ever to install /e/OS on compatible devices! No more juggling tools or tricky steps.
Perfect for flash parties or solo setups—faster, smoother, and more accessible for all!
🖥️ Try it now 👉 https://e.foundation/installer/
📍 Works with Chrome-based browsers like Brave, Chromium & Google Chrome.
#eOS #Installer #Privacy #OpenSource @gael @rikviergever @manojnair @murena
LA PERSONNE GÉNIALE CAPABLE D'EXPLIQUER EN FRANÇAIS, ÉTAPE PAR ÉTAPE, EN N'OUBLIANT AUCUN "DÉTAILLE" DE L'INSTALLATION EST-ELLE SUR D*
15 Comments
14 Likes
2 Comments
1 Shares
2 Likes
1 Comments
One person like that
1 Shares
How to Protect Yourself From the Salt Typhoon #Hack, No Matter What the #FBI Says
source: https://theintercept.com/2024/12/11/fbi-phone-encryption-salt-typhoon/
“If the FBI cannot keep their #wiretap #system safe, they absolutely cannot keep the skeleton key to all Apple phones safe,” Vitka said.
#china #hacker #cybersecurity #encryption #usa #police #surveillance #security #privacy #politics #news #internet #smartphone #communication #chat #online
2 Likes
3 Likes
1 Shares
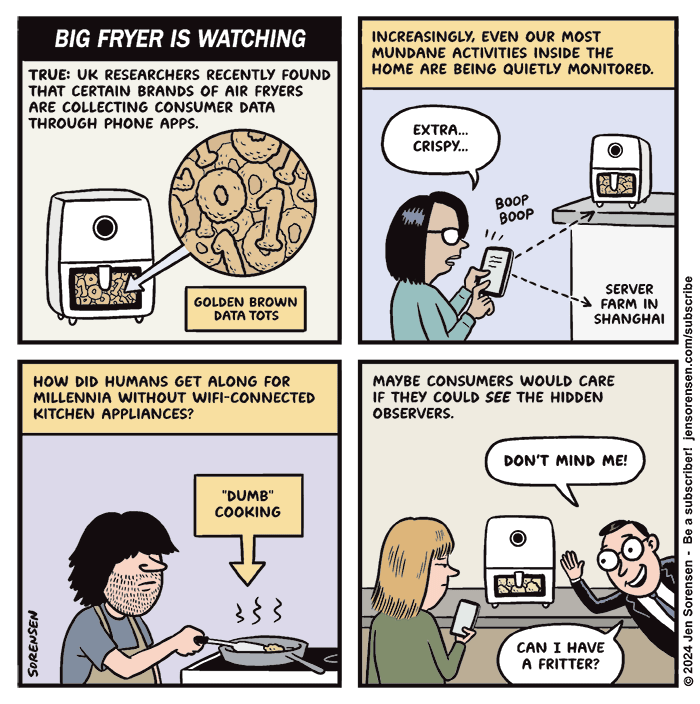
https://mastodon.social/@jensorensen/113653097610306336 jensorensen@mastodon.social - Latest comic. A British consumer rights group examined unnecessary data harvesting by “smart” devices, including air fryers connected to phone apps. While these devices may not pose the greatest privacy risk in our everyday lives, they are part of a growing Internet of Things capable of collecting data when and where we least expect it.
#comic #cartoon #technology #tech #privacy #surveillance #consumer #cooking #internet #internetofthings
3 Likes
2 Likes
1 Shares
EFF Launches Digital Rights Bytes to Answer Tech Questions that Bug Us All

Yes, politicians and Big Corporates do twist narratives to suite their own agendas. EFF is aiming to try to give more objective and honest answers to technology questions, especially those which affect users’ privacy and security.
EFF is the leading nonprofit defending civil liberties in the digital world. Founded in 1990, EFF champions user privacy, free expression, and innovation through impact litigation, policy analysis, grassroots activism, and technology Development. Its mission is to ensure that technology supports freedom, justice and innovation for all people of the world.
An interesting twist is that you can submit your own questions and answers too (without providing your name, e-mail address, or a completed reCaptcha).
See eff.org/press/releases/eff-lau…
#Blog, #EFF, #privacy, #security, #technology
One person like that
Location data firm helps US police find out when suspects visited their doctor
A location-tracking company that sells its services to police departments is apparently using addresses and coordinates of doctors’ and lawyers’ offices and other types of locations to help cops compile lists of places visited by suspects, according to a 404 Media report published today.
Fog Data Science, which says it “harness[es] the power of data to safeguard national security and provide law enforcement with actionable intelligence,” has a “Project Intake Form” that asks police for locations where potential suspects and their mobile devices might be found.
Who needs a surveillance state when the data can just be purchased by the government?
This all comes down to the power of aggregating lots of metadata. If one takes just a single app like WhatsApp where the T&C’s allow for a full range of metadata to be collected by the app and passed upstream to Meta, who leaks data to 3rd parties, it is very easy to see how all this is possible. WhatsApp (just as an example as it is not known whether WhatsApp is the source of this data) knows who you talk to, when you talk to them, where you are exactly, where you live, how often you use your phone, what roads you travel on, where you visit, and lost more. It may not be able to read your E2EE messages, but it knows everything else, and its users have given consent for the data to be passed to 3rd parties.
I really have no idea how such information can be allowed to be traded and sold to interested parties. Many countries only allow such data to be collected and provided to law enforcement after a court order is obtained by law enforcement. As TikTok is still Chinese owned, I’m doubting if this data is being provided by TikTok to US data brokers. It is more likely US owned social networks providing this data themselves (purely my guess, though).
I can see why more and more users are distrusting these companies which provide free services, and then sell their data. The thing is, if law enforcement and governments are buying the data to get around their own legal restrictions, I just don’t see this situation really changing.
As users, we need to shun the use of such services (which is why I deleted my WhatsApp account when the T&C’s changed). It is also worth trying to rather use social networks that fall under the legislation of more privacy-friendly countries. Which also makes me a bit suspicious of why the US wants to maybe force the sale of TikTok to a US company… If that happens, I’ll be deleting my TikTok account too.
It seems more and more to me that social networks are the ideal way to find out who goes where and who they are communicating with… There is certainly lots of economic value in this, otherwise data brokers would not be doing such a roaring trade. They should just be aware though that they are very likely breaking the privacy laws of many non-US countries (not just the EU) if those citizens data is being sold in the USA. It’s time these other countries woke up and took note of what is going on.
See arstechnica.com/tech-policy/20…
#Blog, #privacy, #technology, #tracking
One person like that
2 Shares
Murena Pixel #Tablet - deGoogled services
The #Murena Pixel #Tablet running with /e/OS open source operating system offers a privacy-focused Android experience (de-googled android).
Enjoy the performance and versatility you need, while minimising data tracking, having a more secure experience, and with no #Google services collecting your personal information.
https://murena.com/shop/smartphones/brand-new/murena-pixel-tablet/
One person like that
1 Shares
gb - Chat Control : The EU’s CSAM scanner proposal
fr - La fin de la vie privée dans nos conversations numériques
L’UE voudrait obliger les opérateurs de services de messagerie à chercher de manière automatique les contenus suspects dans les conversations et messages privées ainsi que les emails.
L’objectif déclaré : lutter contre les contenus pédopornographiques (“CSEM”).
Leur solution : la surveillance de masse par la lecture et l’analyse automatique de chaque message envoyé en temps réel, sonnant la fin du secret des correspondances numériques.
Parmi les autres conséquences (qui seront tout aussi inefficaces) de cette proposition de règlement figurent : les blocages réseaux, le filtrage des fichiers privés dans le cloud, la vérification obligatoire de l’âge des utilisateurs mettant fin aux communications anonymes, la censure dans les magasins d’applications, et l’exclusion des mineurs du monde numérique.
#internet #web #réseaux #téléphonie #vie-privée #surveillance #contrôle
#internet #web #networks #telephony #privacy #surveillance #control
One person like that
2 Comments
Russian programmer says #FSB agents planted #spyware on his #Android phone
According to the report, the fake app was able to access location information, read and send text messages, install other applications, read the calendar, take screenshots and record from the video camera, see a list of other applications, answer phone calls, and view user account details — all permissions that the real Cube Call Recorder does not have.
#spy #surveillance #russia #policestate #news #technology #smartphone #Trojan #Software #cybersecurity #security #privacy #Monokle #spyware #Moskow #app
5 Likes
Seit Version 133 connected #Firefox, der selbsternannte #Privacy-Browser schlechthin, beim Start mit jeder Menge Servern, mit einigen davon sogar via http:
34.107.221.82:80
194.45.101.249:443
34.107.243.93:443
34.107.221.82:80
34.149.100.209:443
37.218.242.175:443
34.98.75.36:443
34.117.188.166:443
Bis auf eine gehören alle #Google. Lustig, gell?
6 Likes
5 Comments
Gestemd voor de Big Brother Awards 2024. Op welke privacyterrorist stemt u?
https://www.bitsoffreedom.nl/2024/12/03/wie-verdient-volgens-jou-dit-jaar-een-big-brother-award-2/
Bluesky lost het fundamentele probleem dat het publieke debat in handen is van big tech niet op
Waag Future Lab
De afgelopen weken groeide het aantal gebruikers op Bluesky snel, als alternatief voor X. Maar ook bij dit socialemediaplatform zijn onze digitale publieke ruimte en het maatschappelijk debat vooral een speelbal van private belangen. (...)
> Zie ook: Privacy-experts kritisch over te open karakter van Bluesky
Tags: #nederlands #social_media #sociale_media #fediverse #bluesky #privacy #avg #data #data_mining #debat #publiek_debat #democratie #big_tech #algoritme #mastodon




/cdn.vox-cdn.com/uploads/chorus_asset/file/23318439/akrales_220309_4977_0324.jpg)