#bug
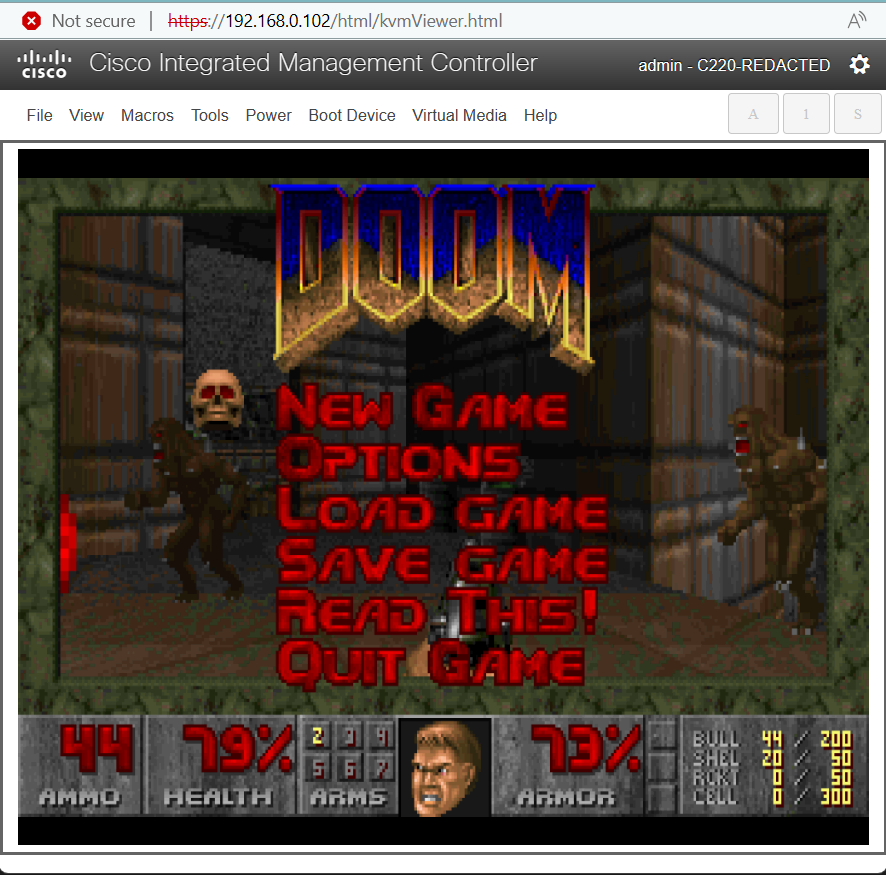
#CVE-2024-20356: #Jailbreaking a #Cisco appliance to run #DOOM
In this adventure, the Cisco #C195 device family was jailbroken in order to run unintended code. This includes the discovery of a vulnerability in the #CIMC body management controller which affects a range of different devices, whereby an authenticated high privilege user can obtain underlying root access to the server’s #BMC (CVE-2024-20356) which in itself has high-level access to various other components in the system. The end goal was to run DOOM – if a smart fridge can do it, why not Cisco?
source: https://labs.nettitude.com/blog/cve-2024-20356-jailbreaking-a-cisco-appliance-to-run-doom/
#software #security #bug #network #game #news #vulnerability #exploit #hack #hacker
#LLM Agents can Autonomously #Exploit One-day Vulnerabilities
Source: https://arxiv.org/abs/2404.08144
To show this, we collected a dataset of 15 one-day vulnerabilities that include ones categorized as critical severity in the #CVE description. When given the CVE description, GPT-4 is capable of exploiting 87% of these vulnerabilities compared to 0% for every other model we test (GPT-3.5, open-source LLMs) and open-source vulnerability scanners (ZAP and #Metasploit).
#ai #technology #Software #chatgpt #bug #hack #news #cybersecurity

Logiciel "Orphée" médiathèque
#surveillance #vieprivée #fichage #biblio #bibliothécaire #logiciel #médiathèque #privatisation #public #informatique #bureautique
Pour situer depuis un peu plus d'un an j'assure des permanences en tant que bénévole à la médiathèque de mon village de 800 habitants.
Mes collègues et moi bataillons avec cet outil en ligne #coûteux, #labyrinthique, qui fonctionne mal, est lourd, difficile à maîtriser même pour les plus expérimentés d'entre nous. Lorsque qu'il y a un #bug les responsables techniques et commerciaux sont injoignables ..
Quant au respect de la vie privée des #usagers, il y a de quoi être vraiment inquiet.
J'aimerais en discuter sur D* avec d'autres personnes concernées par le problème; comment elles y font face ou pas. Ou si elles ont un avis différent sur ce truc..
#NIST National #Vulnerability #Database Disruption Sees #CVE Enrichment on Hold
Since February 12, 2024, NIST has almost completely stopped enriching software vulnerabilities listed in its National Vulnerability Database (NVD), the world's most widely used software vulnerability database.
Source: https://www.infosecurity-magazine.com/news/nist-vulnerability-database/
#nvd #usa #security #software #problem #exploit #hack #bug #news #cybersecurity
#Google don't like C++
Based on this experience we expect that high assurance memory safety can only be achieved via a Secure-by-Design approach centered around comprehensive adoption of languages with rigorous memory safety guarantees. We see no realistic path for an evolution of C++ into a language with rigorous memory safety guarantees that include temporal safety. As a consequence, we are considering a gradual transition of C++ code at Google towards other languages that are memory safe.
Source: https://research.google/pubs/secure-by-design-googles-perspective-on-memory-safety/
#Rust. #Go and #Java will be used.
#software #development #code #language #future #memory #security #bug #exploit #program #news
Hackers exploited #Windows 0-day for 6 months after #Microsoft knew of it
Even after Microsoft patched the #vulnerability last month, the company made no mention that the North Korean threat group #Lazarus had been using the vulnerability since at least August to install a stealthy #rootkit on vulnerable computers. The vulnerability provided an easy and stealthy means for #malware that had already gained administrative system rights to interact with the Windows #kernel. Lazarus used the vulnerability for just that. Even so, Microsoft has long said that such admin-to-kernel elevations don’t represent the crossing of a security boundary, a possible explanation for the time Microsoft took to fix the vulnerability.
#software #news #security #cybercrime #bug #exploit #0day #fail #economy #problem #politics #hack #Hackers #trust #risk
GNOME Is Malicious
So says the MPV (the media player) man page.
I agree. I hate GNOME 3. They also ignore XDG (freedesktop.org) standards.
GNOME is one of the worst offenders, and ignores even the now widely supported idle-inhibit protocol. (This is either due to a combination of malice and incompetence, but since implementing this protocol would only take a few lines of code, it is most likely the former. You will also notice how GNOME advocates react offended whenever their sabotage is pointed out, which indicates either hypocrisy, or even worse ignorance.)\
\
Such incompatible desktop environments (i.e. which ignore standards) typically require using a DBus API. This is ridiculous in several ways. The immediate practical problem is that it would require adding a quite unwieldy dependency for a DBus library, somehow integrating its mainloop into mpv, and other generally unacceptable things.\
\
However, since mpv does not officially support GNOME, this is not much of a problem. If you are one of those miserable users who want to use mpv on GNOME, report a bug on the GNOME issue tracker: https://gitlab.gnome.org/groups/GNOME/-/issues
#gnome #gnome3 #standards #malice #ignorance #screensavers #idle-inhibit #bug #mpv #de #desktop-environment #hypocrisy #sabotage
#Piped #Issue #Issues
Exemple : https://piped.adminforge.de/watch?v=uTrP3escs0s&start=8&end=372
La #vidéo démarre bien à start, mais ne s'arrête pas à end .
The #video starts well at start, but doesn't stop at end .
La page issues : https://github.com/TeamPiped/Piped/issues
Je ne crois pas voir cet item, mais je n'ai peut-être pas assez regardé.... (m'y connais pas trop non plus, pour fouiller dans cette partie)
Si quelqu'un a un compte pour faire remonter le #Bug ?
À noter qu'avec #Invidious, là, la vidéo commence et s'arrête comme demandé.
Exemple : https://yt.artemislena.eu/watch?v=uTrP3escs0s&start=8&end=372
J'en profite pour indiquer que, si sur une page Piped, il pouvait y avoir un lien vers l'URL youtube, ça serait un plus, car ça permet de basculer sur une autre instance Piped ou Invidious facilement, grâce notamment à un #add-on comme #LibRedirect ..
J'dis ça, j'dis rien. :)
Et merci, surtout, à ceux qui ont créé Piped.
#panne #bug #diaspora-fr.org
je ne vois plus les images et vavatars des autres pods, c.est grave docteur???
Hey, let's use #AI to generate #bug reports and #spam the bug trackers of open source projects ...
The I in #LLM stands for #intelligence
source: https://daniel.haxx.se/blog/2024/01/02/the-i-in-llm-stands-for-intelligence/
When reports are made to look better and to appear to have a point, it takes a longer time for us to research and eventually discard it. Every #security report has to have a human spend time to look at it and assess what it means.
#curl #openSource #fail #software #troll #problem #time #news #technology #disaster
They are sharing SSH CVE-2023-48795 (Terrapin attack) vulnerable instances found in their IPv4/IPv6 scans
Nearly 11M instances (by unique IP) found vulnerable (~52%).
Background on the #vulnerability: https://terrapin-attack.com
fedivers: https://infosec.exchange/@shadowserver/111691389140858555
#cve #network #internet #security #bug #cyberwar #software #terrapin #attack #danger #administration #update #patch #ssh
A giant crawling #brain: the jaw-dropping world of #termites
Back in the 1930s, the other Marais didn’t write a #termite #science book, but a book about how humans could understand termites – as a #bug, a #body, a #soul, a force on the #landscape. Looking at termites this way changed how I see the #world, science, the #future and myself.
#Lazarus Group Is Still Juicing #Log4Shell, Using RATs Written in 'D'
source: https://www.darkreading.com/threat-intelligence/lazarus-group-still-juicing-log4shell-rats-written-d
Two years on and multiple “the sky is falling” headlines later, Veracode reported last week that more than a third (38%) of all in-use applications are still using vulnerable versions of #Log4j.
#software #fail #bug #security #NorthKorea #attack #problem #news #cybersecurity #update #economy