#onion
#Evening #flowers
In direct evening #sunlight, these flowers are from an #onion #plant and you can see they're about to bloom. They usually attract #bumblebees, #bees and other #pollinators. At the back you can still see the casing that is still partially attached to the stem,

Here's another bunch of #florets (sorry I don't know what plant it is) with a #fly feeding on them.

#MyWork #MyPhoto #CCBYSA #DSLR #Nikon #D7000 #Summer #Horticulture
You can now sign up for your Proton account directly on our onion site, making it even easier for anyone to use Tor to bypass censorship and set up a #Proton account.
source: https://protonmail.com/blog/updated-tor-site/
#tor #onion #news #censorship #communication #freedom #darknet
If you want to use a secure #browser but have no idea at all, which one do you use?
I don't mean the following text in a negative way, because you can't expect every Internet user to have studied #computer #science beforehand in order to be able to evaluate the security of #software correctly. Safety, like truth, is in the eye of the beholder. Some people think it's great to get targeted #ads and just don't want to be trojanized when paying for online shopping. A #whistleblower, on the other hand, would prefer not to leave any usable traces on the #Internet at all.
How can you decide now, even without studying, whether one browser is more secure than another?
Some time ago I recommended #Librewolf ( https://librewolf.net ) as a browser and immediately got disagreement in the comments: https://despora.de/posts/ddc445606a79013af2e2543d7eeced27
Here is the article out of the comments that now really clearly states that Librewolf is not a secure browser: https://www.unixsheikh.com/articles/choose-your-browser-carefully.html#librewolf <- I think the whole article is bad unprofessional propaganda :(
Every software contains more or less serious security vulnerabilities in certain versions. Without an indication of which version was tested and whether these vulnerabilities were closed in the next version, the accusation is worthless. Every browser makes contact with numerous IP addresses, which is the whole point of its existence. Without knowing what is behind these IP addresses and whether they offer useful services, a beginner cannot evaluate whether they are dangerous. An example: The browser checks every web page for viruses at #Google. This increases the #security for the surfer to get Trojans or worse, but Google also gets the entire browsing #history and can evaluate it. You have to classify the whole thing and also say why you rate things as bad or good.
So instead of Librewolf, #GNU #IceCat is recommended there, among other browsers. Is this a good advice?
I don't think so, since IceCat itself always adds important security #updates very late due to an complex build process ( https://www.mail-archive.com/bug-gnuzilla@gnu.org/msg03934.html ).
So let's use the #TOR browser, which is always up to date and is even recommended by #Snowden.
You can do that and I have also recommended the TOR browser in certain situations. But if you have no idea for which specific problem the TOR browser was developed in the first place and you can't understand the term #darknet, you might end up with more problems than you gain in security. But if you know that TOR stands for the #onion router and that the onion is just a metaphor for a routing protocol, then you surely know how to set up a secure exit node and how to minimize dangers.
If you question everything, you never come to a conclusion?
As I said, safety is in the eye of the beholder but there are some guidelines that are universally valid when evaluating. The browser should be made of free open source #software ( #FLOSS ), even if this alone is not a security feature. Free software just means that anyone can search the source code for security holes and backdoors, and that independent trusted vendors can compile the browser for me. However, in order to maintain this safety gain, this work must be done. Since it is time-consuming and usually poorly remunerated, this unfortunately happens far too rarely.
That is why automated tests are used. These are better than nothing, but only find known security problems. An automated test cannot find a backdoor injected by a secret service. The results of such automated tests can be found here: https://privacytests.org/private.html
Looking at the security of the TOR browser in the test result, one might conclude that it is better to use another more secure browser on the darknet. This is dangerous because one security feature on the darknet is that everyone has the same browser fingerprint, and if you don't use the TOR browser you are easier to track because of a different fingerprint.
Long speech short sense. I trust you and take the Librewolf.
On #Windows, Librewolf is a poor choice because it has no automatic #update process. Let's face it, beginners tend to forget to keep their software up to date. On Windows, it's better to use the original #Firefox, which updates itself automatically.
Firefox or Librewolf can be further improved in terms of security with add-ons.
One thing in mind is that every add-on slows down the browser and increases the probability of catching additional security vulnerabilities. Software is always complex and more software increases complexity and decreases security.
If you have no idea, please use only verified add-ons. Fortunately, this is very easy with Firefox, because you only have to check for this sign:

https://support.mozilla.org/en-US/kb/add-on-badges#w_recommended-extensions
I have gathered here some add-ons that are verified and increase your security. Please install them only if you know exactly what these add-ons do and if you need them.
https://addons.mozilla.org/en-US/firefox/collections/17383777/Privacy-4-U/?page=1&collection_sort=-popularity
#knowledge #privacy #surveillance #tracking #news #Recommendation
Does anyone of you work at "La Quadrature du Net" (LQDN)?
It's a French #NGO fighting for a free Internet. They have a #Jabber / #XMPP server running with a wrong configuration at: https://jabber.lqdn.fr - The #onion address of the server must be changed to a V3 address since the latest update of #TOR. Then the new onion address must be entered here: https://jabber.lqdn.fr/access-our-chat-server-using-tor-and-onion-address - Such an onion address is important for the anonymity of whistleblowers, because they don't want their IP logged.
#lqdn #France #problem #information #configuration #followerpower #attention #danger
How to send a #password securely over an unsecured #connection
A relatively common task for me as a hacktivist is to set up secure #communication channels for technologically innocent newbies. I could of course explain to them how #GPG works, but this often fails due to the lack of will to understand and download and install the programs. Very often I use #XMPP server inside the #onion network (TOR) for #communication. The target must install the Tor #browser for this and can then use an XMPP web client. I can set all that up. The only problem is how do I send the authentication data for the XMPP access securely over an unencrypted connection?
I use #PrivateBin for this #problem: https://privatebin.info
PrivateBin is a #PastBin with encryption and burn after reading features. I post a message on PrivateBin with all the information and burn after reading. The message is encrypted and can only be decrypted with a parameter send together with the URI. The URI can look like this:
https://privatebin.net/?55ac2c8792cb12b9#3fQw1R8SAAQUUGsoa7nDdkYwq34Pzw6GQeSA56v5nusq
If the user can log in, then the authentication data has reached him without being compromised. After that, everything else can be discussed over an encrypted connection. If the user cannot log in, the data may have been intercepted. If you operate the PrivateBin server yourself, you can see which IP has accessed it. You should change the XMPP server and create new authentication in this case.
It can happen that with a weak internet connection the page cannot be loaded completely and when you press reload, of course it doesn't work because the page only works once due to the "burn after reading". Then you have to send the whole thing again with a newly generated URI. But if this does not work several times you should be very careful. Secret service agents like to play the fool in order to tempt you to use unsecured communication channels that are easier for them to wiretap.
#wisdom #knowledge #internet #instruction #security #privacy #surveillance #encryption
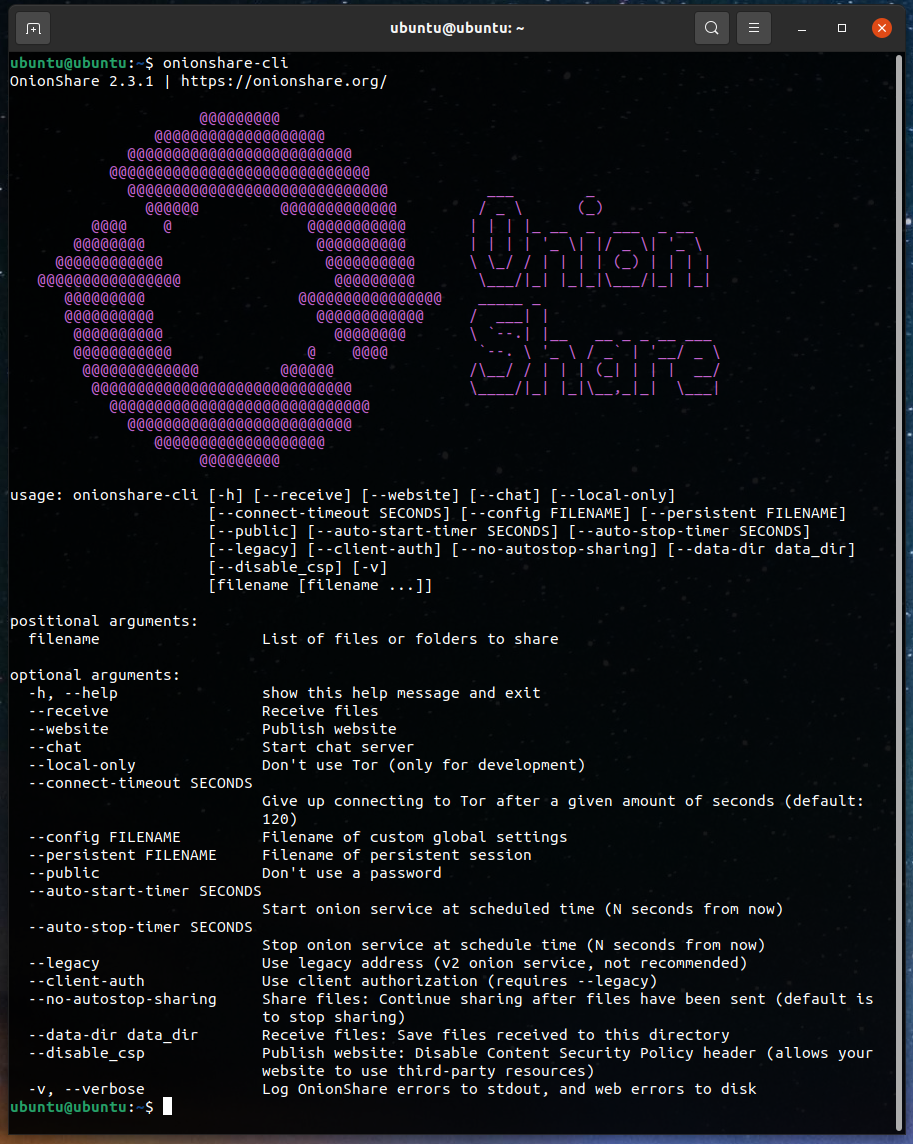
Portable-Onion-Site Version 1.8 Is Published
This is all you need to create a portable, static, self-hosted, Tor Onion Service Website.
This version just upgrades Tor to version 0.4.6.8.
https://archive.org/details/portable-onion-site
This is a kit, in the form of a signed, but not encrypted, Tar archive that contains all you need to create a portable, static, self-hosted Tor Onion Service website. The webserver is a modified darkhttpd.
Download https://archive.org/download/portable-onion-site/portable-onion-site.gpg and then
- Drag and drop it onto EasyGPG or
- In a terminal window,
gpg portable-onion-site.gpg, and then unpack the resulting Tar archive namedportable-onion-site.
Files
My Public Key https://archive.org/download/portable-onion-site/57b731e9.asc
README https://archive.org/download/portable-onion-site/README
The Whole Package https://archive.org/download/portable-onion-site/portable-onion-site.gpg
#portable-onion-site #tor #onion #website #onion-service #hidden-service #tor-onion-service #tor-hidden-service #censorship #onionland

These #Search Engines are best for your #Privacy:
- SearX -> http://z5vawdol25vrmorm4yydmohsd4u6rdoj2sylvoi3e3nqvxkvpqul7bqd.onion/
- search.brave.com -> https://search.brave4u7jddbv7cyviptqjc7jusxh72uik7zt6adtckl5f4nwy2v72qd.onion/
- AHMIA.fi -> http://juhanurmihxlp77nkq76byazcldy2hlmovfu2epvl5ankdibsot4csyd.onion/
- DuckDuckGo.com -> https://duckduckgogg42xjoc72x3sjasowoarfbgcmvfimaftt6twagswzczad.onion/
- OnionSearchEngine.com -> http://kn3hl4xwon63tc6hpjrwza2npb7d4w5yhbzq7jjewpfzyhsd65tm6dad.onion/

Umstellung der Adressen im Tor-Netzwerk
Tschüss nnksciarbrfsg3ud.onion
In den nächsten Tagen wird unser Webauftritt im Tor- oder .onion-Netzwerk mit der Adresse nnksciarbrfsg3ud.onion abgeschaltet. Natürlich wollen wir weiter auch im "großen Internet" vertreten sein. Man wird uns dann unter der etwas längeren Adresse
http://a6pdp5vmmw4zm5tifrc3qo2pyz7mvnk4zzimpesnckvzinubzmioddad.onion/
finden.
Der Grund für diese Umstellung ist eine Erhöhung der Sicherheit im Tor-Netzwerk. Die "kurzen" Adressen der Version v2 werden zum Monatsende ungültig. Der aktuelle Tor-Browser kann dann nur noch Adressen der Version v3 öffnen.
Da sich sowieso niemand solche Adressen weder in v2 noch in v3 merken kann, ist das für die Nutzer eigentlich egal. Immerhin fängt unsere Adresse für A-FsA mit einem "a" an, gefolgt von einer "6" und "F" ist der 6. Buchstabe im Alfabet - hilft wohl auch nichts ... ;-)
Auf jeden Fall ist eine Webpräsenz im sogenannten "Darknet" wichtig, um auch anonym für alle Menschen erreichbar zu sein - egal welche Regierung sie gewählt haben oder erdulden müssen. Also denkt immer daran, dass man mit einem normalen Browser nur die Oberfläche des Internet (-Ozeans) sehen kann, für einen Blick in die Tiefe und die Möglichkeit anonym zu Surfen ist der Tor-Browser unerlässlich.
PS. Der oben angebene Link funktioniert nur mit einem Tor-Browser - und hat momentan noch ein Zeichenkodierungsproblem bei Umlauten - nächste Woche wird es lesbarer - versprochen!
Hier geht es in unser "Darknet" bei http://a6pdp5vmmw4zm5tifrc3qo2pyz7mvnk4zzimpesnckvzinubzmioddad.onion/
Link zu dieser Seite: https://www.aktion-freiheitstattangst.org/de/articles/7770-20210916-umstellung-der-adressen-im-tor-netzwerk.htm
Link im Tor-Netzwerk: nnksciarbrfsg3ud.onion/de/articles/7770-20210916-umstellung-der-adressen-im-tor-netzwerk.htm
Tags: #Umstellung #Adressen #Tor #Netzwerk #Internet #Darknet #onion #Versionswechsel #Browser #Verbraucherdatenschutz #Datenschutz #Datensicherheit #Lauschangriff #Überwachung #Abwehr #Transparenz #Informationsfreiheit #Anonymisierung #Meinungsfreiheit #Pressefreiheit #Internetsperren #Netzneutralität
Just a small part of the excellent #onion #crop at #thehaciendamustbebuilt this year. Been eating them for weeks now, but it’s time to bring in the rest and string them up https://www.youtube.com/watch?v=6vFBaSUVxAA
#homesteading #gardening #self-sufficiency #food #anarchism #cosecha #cebollas #Galiza #Galicia
Starting October 15, all V2 #Onion addresses will be deactivated.
Source: https://blog.torproject.org/v2-deprecation-timeline
October 15th, 2021 - We will release new Tor client stable versions for all supported series that will disable v2.
This is an example for a V2 Onion URI: 5rgdtlawqkcplz75.onion
This is an example for a V3 Onion URI: ynnuxkbbiy5gicdydekpihmpbqd4frruax2mqhpc35xqjxp5ayvrjuqd.onion
If you're still using the short V2 URIs please #update now to V3.

#Darknet #Tor #URI #Warning #Attention #News #Timeline #Security #Privacy
#onion-site #tor #onion #website #static-website #onion-service #hidden-service #tor-onion-service #tor-hidden-service #onionland #tor-browser #torbrowser
Ich kann's einfach nicht lassen. Seit geraumer Zeit publiziere ich wieder mein blöglein
über einen #tor-hidden-service unter
http://w45jxacxizahnu6jjcycave56z3rxqthnsnwu5zcayidyngyqvhqzbyd.onion/
Aktuell rennt bei mir Version 0.4.6.1-alpha !!!
Major features (control port, onion services):